Blog
Flashpoint Year In Review: 2022 Breaches and Malware Threat Landscape
This blog is part of our 2022 Year In Review, an intelligence retrospective highlighting the most significant trends of the past year—plus insight into 2023.

KEY TAKEAWAYs
This blog highlights trends in notable observed advertisements on illicit forums for breached data, including databases or claims of network access; hacking services; and various strains and types of malware from January 1, 2022 through November 30, 2022.
-The most frequently reported-on targeted sectors in 2022 were the government, financial, and retail industries
-The United States was the most-targeted geographic region in breach reporting this year
-Threat actors most commonly advertised and discussed hacking services, malware, and exploits on the popularly used forums Breach Forums, Exploit, and XSS.
-Phishing pages were some of the most popular offerings within hacking services and malware advertisements.
Data breach landscape
Mostly motivated by greed, threat actors will target any organization regardless of sector. Therefore, data breaches provide key insights into the methods and tactics of hackers—since they will do whatever it takes to gain illegal access into their target’s network—using the plethora of advertised malware and hacking services available on illicit marketplaces.
As such, studying data breaches can help organizations and their security teams improve their security controls and incident response plans. Understanding who breaches affect, as well as where they take place, helps you gain visibility into your risk profile.
Here’s how the data breach landscape played out in 2022.
Most impacted sectors
According to our research team, there were a total of 4,146 reported global data breach events that occurred this year. Of those events, the top three sectors that experienced the most breaches were government, financial, and retail:
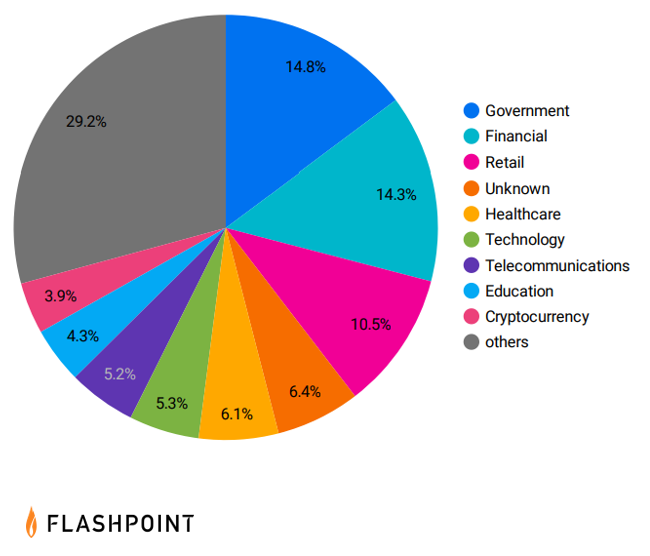
However, although sectors such as Healthcare and Technology also had been impacted by breach events, there was a fourth category that experienced the next most activity—”Unknown.” The unknown category represents datasets (whether advertised or leaked) where the victim’s identity was unavailable—either because that information was not disclosed, or because the data itself or the shared sample lacked any kind of identifiable information.
Government
On par with last year’s findings, government-related breaches and advertisements of access prevailed as the most populous compared to other sectors. However, readers should be aware that while many threat actor advertisements on illicit marketplaces did contain datasets or information specific to government agencies, many breaches were classified as “government” due to records containing specific information provided by governments—such as Social Security numbers, drivers licenses, passports, and other government-issued documents.
Financial and retail
Financial and retail-related data breaches and advertisements for access were the second and third most mentioned sectors in this year’s reporting. Analysts assess that this is at least in part due to financially motivated threat actors seeking to steal sensitive financial and customer information.
In addition, Flashpoint analysts also observed a relatively high volume of Exploit auctions for sets of financial “fullz” (full sets of credit card information), as well as access to retailer e-commerce platforms and content management systems.
Within retail network access advertisements, most threat actors specifically shared how many online orders were paid with a credit card, highlighting the value that credit card information has to threat actors.
Healthcare
Traditionally, healthcare information has been one of the most popular advertisements within breach reporting—however, healthcare advertisements have dropped slightly from last year. This trend is likely heavily influenced by the increasing sharing of healthcare data, as opposed to the selling of it within illicit communities. It is not immediately clear as to why this is occurring, but Flashpoint analysts note that it may indicate that breached or compromised healthcare data is increasingly being used by those who initially stole it.
Despite the drop of advertisements, this does not imply that the healthcare sector experienced fewer data breaches. According to Flashpoint’s Cyber Risk Analytics (CRA) offering, the healthcare sector is still heavily breached by threat actors:
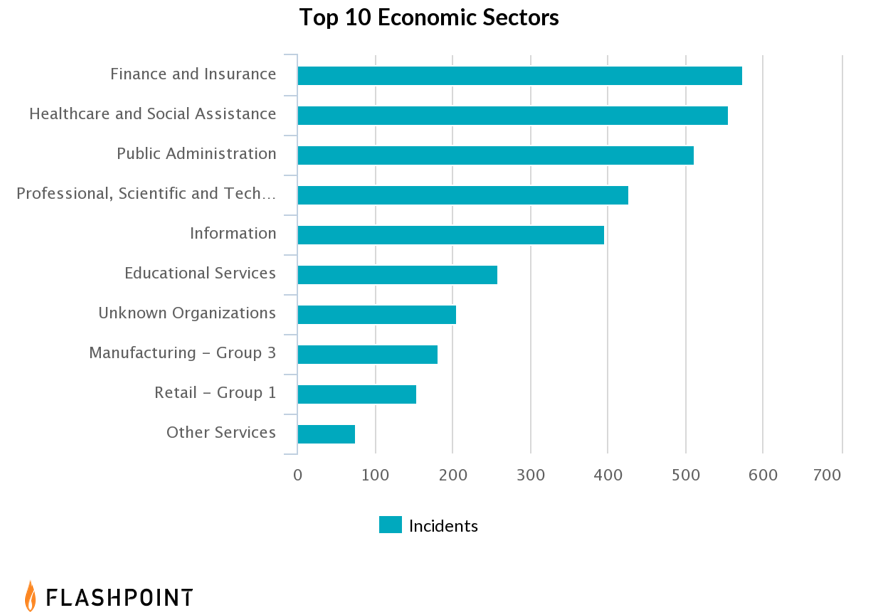
The drop of healthcare related advertisements, coupled with the high number of observed healthcare breach events, further strengthens our hypothesis that successful threat actors are likely choosing to not immediately promote this information within illicit communities. Additionally, the healthcare sector in the United States is subject to strict data breach reporting rules by the Department of Health and Human Services, which may help account for the overall volume of reported healthcare breaches.
Most targeted countries
Sellers within marketplaces and on illicit forums are increasingly disclosing the geographic locations affiliated with their advertisements of datasets or of access. This has in turn led to the “unknown” category accounting for only a negligible percentage when it comes to the location of breach events.
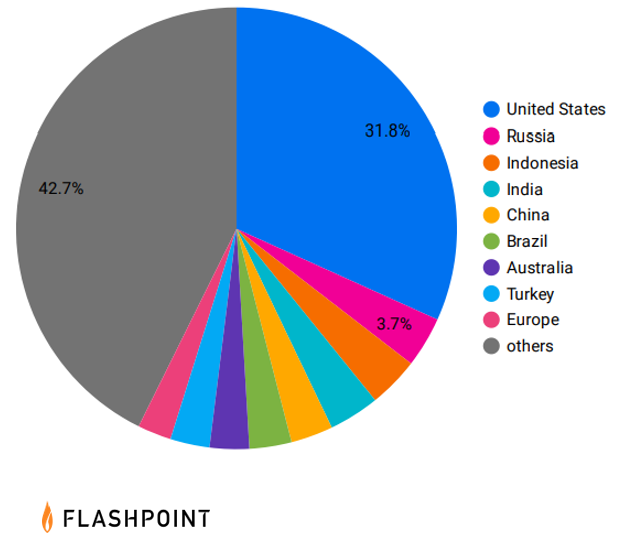
The United States persisted as the top targeted country year-to-date. Based on Flashpoint’s collections and reporting, the most commonly exploited sectors within the United States were government, financial, and retail.
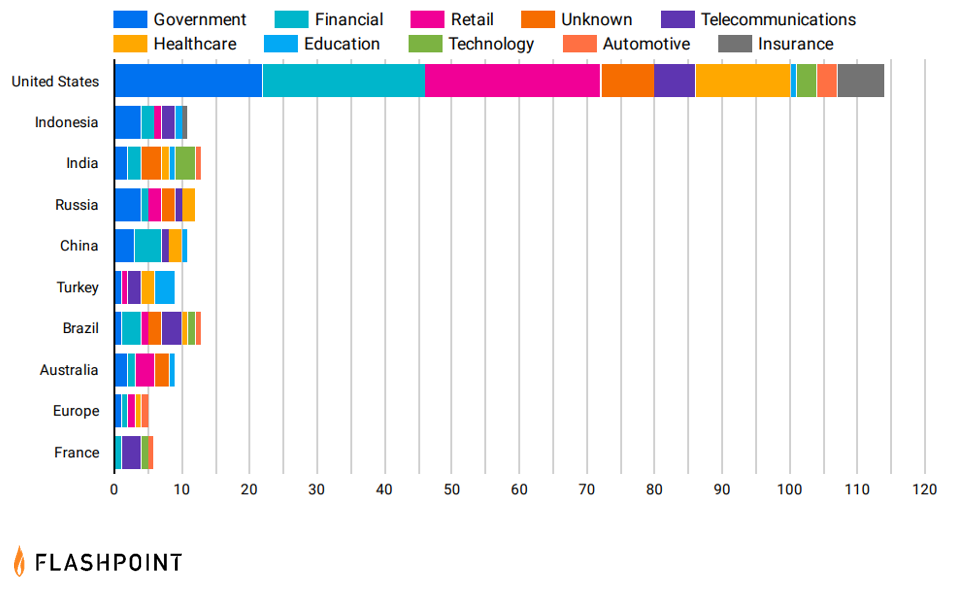
However, readers should be aware that in some advertisements, threat actors explicitly stated that they do not target “CIS” (Commonwealth of Independent States) states, which may suggest a loyalty to or an affiliation with Russia—which could help explain the mass targeting of US entities.
Malware and hacking services
Between January and November 2022, threat actors most commonly advertised and discussed hacking services, malware, and exploits on XSS, Exploit, and Breach Forums. This year, two marketplaces were among the top ten sources for malware and hacking mentions: Alpha Bank Logs and Abacus.
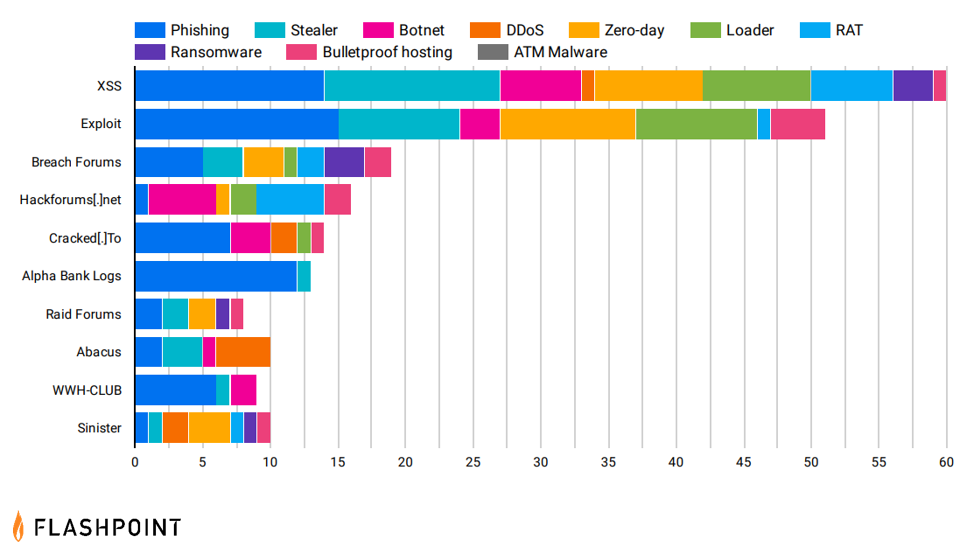
Compared to last year, phishing and infostealer malware were the two most discussed hacking services and malware in 2022.
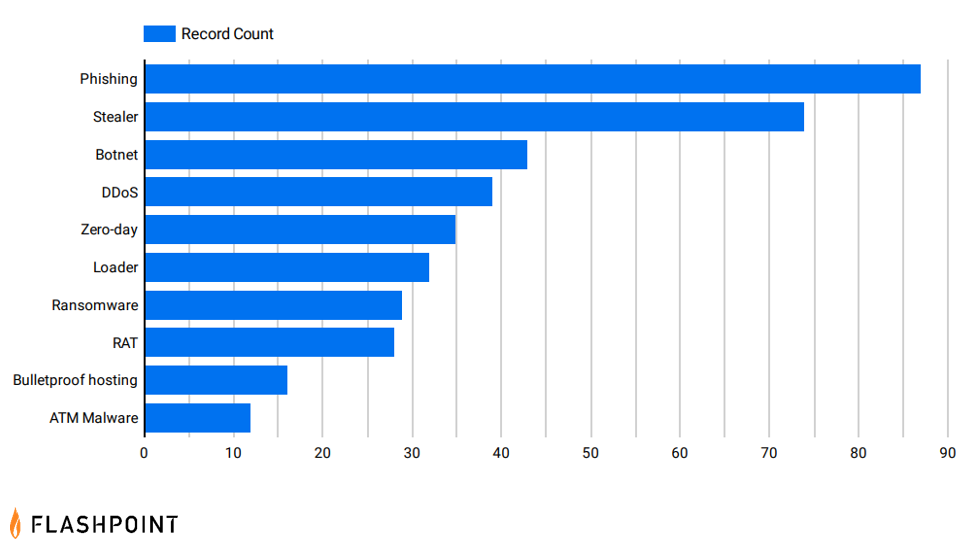
Phishing
Phishing was the most advertised type of malware and hacking service this year. Advertisements for and solicitations of phishing pages or services commonly took place within Flashpoint’s marketplace collections—specifically on Alpha Bank Logs—a clearnet financial fraud market.
Distributed Denial-of-Service (DDoS)
Distributed Denial-of-Service (DDoS) attacks were prominent this year, both within Flashpoint collections, and in public reporting. Earlier in the year, the spike of globally observed DDoS attacks could be traced to political tensions and hacktivism exacerbated by the Russia-Ukraine War. According to research by Radware, the first six months of 2022 saw a surge in DDoS attacks, citing a 203 percent increase in 2022 H1 compared to 2021 H1.
In addition to direct advertisements and solicitations for services involving DDoS, those including botnets, and bulletproof hosting may also be affiliated with launching a DDoS attack.
Ransomware
The majority of ransomware advertisements and solicitations took place on Breach Forums this year. This may in part be due to the fact that in 2021, XSS, as well as some other Russian-speaking forums had banned advertisements for ransomware—due to unwanted attention from law enforcement, in response to attacks on critical infrastructure.
Protect your data and assets with Flashpoint
Flashpoint’s suite of actionable intelligence solutions enables organizations to proactively identify and mitigate cyber and physical risk that could imperil people, places, and assets. To unlock the power of great threat intelligence, get started with a free Flashpoint trial.