
Data breaches are invaluable to understanding a threat actor’s goals and motivations. Often fueled by financial gain, malicious actors, as well as Advanced Persistent Threats (APTs), will do whatever they can to gain illicit access into susceptible organizations—employing a wide array of underhanded tactics, such as phishing or exploiting vulnerabilities.
Studying breach events can help CISOs and their security teams improve their incident response processes by examining trends, as well as extrapolating how a potential attack could impact their organization. Furthermore, understanding how and where they occur can help security and intelligence teams understand their risk profiles and potentially prevent them from happening.
In this article, we:
- Define the term “data breach”
- Describe how data breaches occur
- Explain how threat actors operate and the information or access they’re after
- Provide examples of public large-scale data breaches
- Outline defend against a cyber attack, and how to prepare a response plan
What is a data breach?
A data breach occurs whenever sensitive data is unintentionally exposed, or when an unauthorized entity leaks, or steals it. Breach events can occur by accident, through negligence, or they can result from a targeted attack. A breach incident could range from one to over 1 million records of breached data. However, over the past few years breach events have begun to expose billions of records containing sensitive data and customer information.
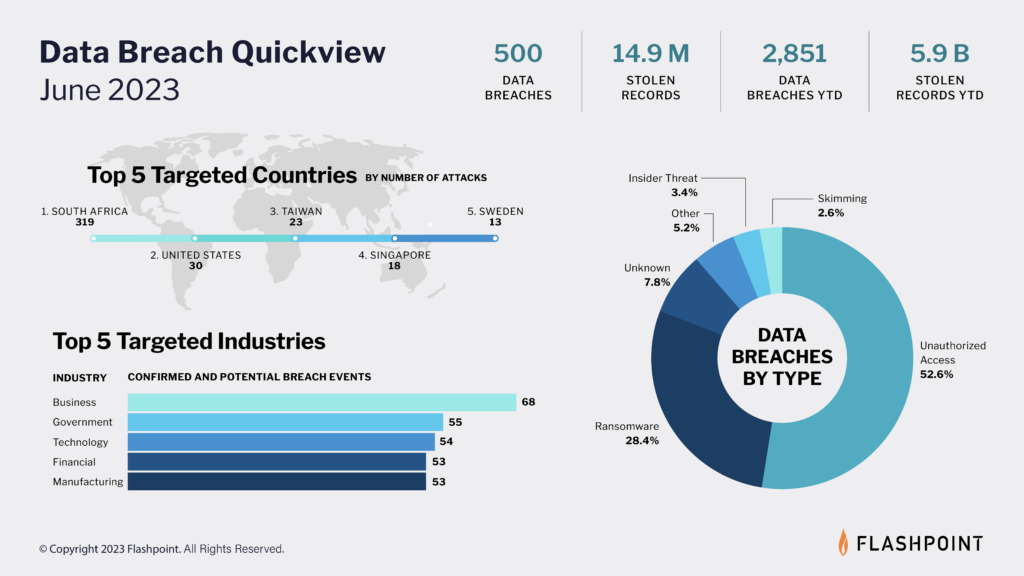
How do data breaches occur?
“Hacking,” the unauthorized access to systems or services, has been the driving factor for reported breach events—being the number one reported breach type for over the past 10 years. Malicious actors use a combination of social engineering techniques, in addition to exploiting vulnerabilities in order to leverage illegal access into an organization’s network.
However, while most impacted organizations are quick to claim that they fell victim to a “sophisticated cyber attack,” research shows that breaches that have exposed the most records are the result of human error—stemming from poor security controls and unpatched system vulnerabilities.
Poor security controls have been responsible for billions of exposed records
Misconfigured databases and weak security best practices resulted in 19.81 billion records being exposed last year. Threat actors are continuously scanning the Internet for exposed databases that are available to the masses via search engines and public-facing pages. Oftentimes, these databases have poor password security, or lack 2-factor authentication, thus being discovered by either security researchers, or threat actors who then advertise their existence on illicit forums.
Threat actors exploit vulnerabilities to gain illegal access
On the other hand, malicious actors also scan a potential victim’s network looking for vulnerable assets—then using that information to weaponize vulnerabilities by using exploits. Once compromised, threat actors can either choose to move laterally within the system, or install ransomware to steal data.
As such, vulnerability intelligence is critical to mitigate risk, since vulnerability management processes are dependent on it. However, organizations cannot rely on publicly available sources like CVE or NVD, since they are completely unaware of nearly a third of known risk. Security teams will need a comprehensive source of vulnerability intelligence to remediate effectively, since according to Dark Reading, nearly every application has at least one vulnerability or misconfiguration that compromises security in some way.
What type of data do hackers steal?
Any kind of private data can be involved in a data breach, however, threat actors often seek personally identifiable information (PII) since it can be easily sold on illicit marketplaces. Breached PII often includes:
- Names
- Email addresses
- Passwords
- Addresses
- Date of birth
- Social Security Numbers
- Drivers license numbers
- Credit card information and other financial data
There are some situations where PII is not the main target. In these scenarios, the attacker is usually revealed to be an APT, hacktivist, or some other highly-skilled threat actor who is after specific information. Such information can include:
- Classified government documents or communications
- Internal business information, such as trade secrets
- Proprietary source code
- Infrastructure data
What are the biggest breaches of all time?
Any organization, regardless of size or industry is at-risk of experiencing a data breach. The following are the top three largest breaches known so far:
1. FSB Markets, Inc.
Online forex broker FBS Markets Inc. exposed approximately 16 billion records which included names, email and physical addresses, passport numbers, identification verification documents, trading histories, and more. The data was left in an unsecure database and later leaked online. This breach was discovered in 2020, but FBS Markets, Inc. didn’t publicly report this incident until March 2021.
2. CAM4
10.9 billion records were exposed via a misconfigured database, potentially leaking the names, email addresses, IP addresses, payment logs, and chat transcripts of CAM4 users, an adult streaming site specializing in amateur webcam shows.
3. Le Group Figaro
A French newspaper, Le Figaro left nearly 7.4 billion records wide-open in an unsecured database which housed employee information, addresses of their subscribers, IP addresses, and more.
How organizations can prevent data breaches
“Comprehensive and repeatable processes for hardening systems, coupled with periodic audits of controls can substantially reduce the likelihood of a large scale data leak.“
State of Data Breach Intelligence, Flashpoint
Prevention is the ideal data breach scenario for any organization. For cases involving human error, such as misconfigurations and social engineering campaigns, educating personnel and implementing security best practices goes a long way.
Security teams also need to ensure that they are patching vulnerabilities regularly, especially focusing on deployed assets that house sensitive data. Having a comprehensive source of vulnerability intelligence such as VulnDB is crucial, since Vulnerability Management teams need detailed intelligence that contextualizes risk to their assets. In addition, VulnDB also gives security teams the ability to predict which vulnerabilities could be used in future ransomware attacks, empowering them to thwart threat actors.
Enterprises should also assess and improve their third-party vendor security, making sure that everyone within their supply chain is taking security seriously. In today’s business landscape, data is often being shared between multiple organizations and recent cyberattacks demonstrate that a weak link in your digital supply chain can introduce a risk aperture that can be difficult to detect or address.
The importance of incident response
However, business leaders should not focus solely on pre-emptive measures. Resiliency and having a well-developed incident response plan is just as important. If organizations find themselves compromised, they will need to contain the threat and respond quickly. Effective containment and response strategies can involve:
- Locating, repairing, and securing affected systems
- Reporting the breach to a regulatory authority
- Informing affected individuals
- Rely on cybersecurity and digital forensics experts to gather appropriate threat intelligence to better understand how the system was compromised
- Improving security processes to prevent future attacks
Prevent and respond to data breaches with Flashpoint
Data breaches can have a serious impact on any organization and data shows that anyone can become a potential victim. Flashpoint Professional Services (FPS) offers a Threat Response and Readiness Subscription that helps companies prepare for and respond to a ransomware or cyber extortion attack. But for security teams seeking to get in front of ransomware events, organizations will greatly benefit from our newly introduced Ransomware Prediction Model—which provides a Ransomware Likelihood score for over 300,000 vulnerabilities. Contact us and sign up for a free trial today.