Blog
Definitive Guide to Ransomware: What It Is and How Your Organization Can Prevent, Detect, and Respond to a Ransomware Attack
A guide to defining, explaining, and understanding ransomware to bolster your organization’s security posture against attacks.

Understanding Ransomware
Ransomware threats have become a relevant part of any organization’s risk landscape awareness in the past few years as threat actors and their TTPs become more advanced and take on a more diverse range of targets. Understanding what ransomware is, what risk it presents for your organization, and how to build an effective response and recovery plan are all crucial for implementing a strong threat intelligence program and keeping your assets, infrastructure, and personnel secure.
In this article, we:
- Define ransomware and overview its history, including notable attacks
- Outline types of ransomware and how attacks occur
- Explain what measures your organization can take to remediate ransomware risk and respond and recover to an attack
What is ransomware?
Ransomware uses data encryption to block organizations’ access to their own sensitive data, demanding a ransom is paid to unlock it safely. Personnel facing a ransomware attack are denied access to internal files and programs, and ransomware actors often design their malware to spread throughout an organization’s infrastructure while targeting its entire database and file servers, more effectively forcing the company to pay the ransom.
As attacks evolve to become more severe, threat actors have also adopted tactics to add external pressures, such as threatening to release confidential information, doxx executives, or inform clients that the company is not willing to pay to protect their data, to increase the likelihood of payment.
History of ransomware
Although it’s become increasingly discussed in the past decade, ransomware attacks have existed for almost 40 years. One of the first recorded ransomware attacks, taking place in 1989 and released via floppy disk, was the AIDS Trojan—also called the PC Cyborg Virus. This ransomware attack demanded that victims send $189 via post to a P.O. box in Panama to restore access, although the encryption strategy used would not be effective at locking organizations out of their own systems today.
Until the 2000s it was difficult to efficiently receive ransom payments, making ransomware attacks relatively rare compared to today. Threat actors usually collected payments through money transfer services like Western Union or MoneyGram, or would request users to send prepaid debit cards through services like MoneyPak. With the advent of cryptocurrency, it has become much easier for threat actors to receive payments and quickly profit, which has led to this type of attack becoming more widespread.
The advancement of ransomware
Ransomware’s evolution has seen a shift in the way threat actors choose their targets and tailor their attacks. In the past, “general” ransomware attacks were more common, and would target wider groups of victims at once to take advantage of a larger volume of lower value payments. They were fairly random, and would prey upon whoever happened to download the malware that would force them to pay.
However, extortionist sites, like the one associated with the criminals behind Maze ransomware, have given threat actors the ability to effectively target specific entities that are willing to pay higher ransoms in a single attack. Victim-shaming sites prevent targeted organizations from keeping an attack private and taking their time to pay the ransom, which makes them more willing to pay and helps the perpetrators profit quickly and with a higher success rate.
As ransomware attacks become more advanced, many threat actors have also begun leveraging other tactics in addition to holding confidential data hostage to further encourage organizations to pay up quickly. One of the most common secondary threats is to release the private information they’ve captured, either to the general public or to a company’s board, further damaging an organization’s reputation in the wake of an attack.
Flashpoint has observed up to four tactics used in a single attack, often progressing from the aforementioned data encryption and theft to DDoS attacks, which shut down the victims’ sites so customers cannot get service, and harassment, which involves the threat actors directly contacting customers, investors, and the media to publicize the attack.
As a result, ransomware attacks often disable organizations and leave them unable to move forward without giving into demands, which is why ransomware has become a growing issue for companies as more threat actors attempt to profit from this lucrative threat vector.
This cybercrime industry is expected to grow to over $265 billion by 2031, and has become a risk for organizations across categories that must be considered as organizations build their threat intelligence and risk remediation programs.
How does ransomware work?
Essentially, ransomware is built to infiltrate an organization’s system, encrypt the files so they’re inaccessible to other users, and send a ransom demand to the victim. There are several ways threat actors accomplish these steps, but they are most often broken into the following components:
Distribution and infection tactics
In order to gain initial access to a system, threat actors leverage a variety of infiltration vectors to help them infect an organization’s database. Some of the most common include:
- Phishing emails: Members of an organization are sent emails from outside the company that contain links with harmful malware attached. The email includes a message encouraging the recipient to click the attached link, normally under the guise of being for a legitimate purpose, and the ransomware can then infect the system.
- Drive-by downloading: Members of an organization unknowingly visit websites that contain malware, which can then spread to their local device and infiltrate company infrastructure, allowing ransomware to encrypt its data.
Recommended: Where Do Cybercriminals Stand on Ransomware Now?
- Remote desktop protocol (RDP) compromise: A threat actor who is able to obtain a user’s login credentials for their device can remotely authenticate and log into a computer within an organization’s network. From there, they can control the device and download malware to execute a ransomware attack.
- Direct infiltration: Some ransomware attacks involve threat actors directly hacking into an organization’s network, allowing them to infect company infrastructure themselves. They specifically target unpatched systems that leave an organization open to vulnerabilities that make it easier for attackers to distribute the malware needed to execute a ransomware attack.
Ransomware attacks often make use of multiple tactics to achieve the required level of access necessary to execute a large-scale attack.
File and data encryption
Once an organization’s infrastructure has been compromised, ransomware actors must encrypt the data so it is inaccessible to others and can be used to leverage payment for its unlocking.
This part of an attack is often the most straightforward, since encryption functionality is built into an operating system. It involves accessing the files—which is possible with the previously-installed malware—and then encrypting them with a unique attacker-controlled key. These new files replace the old ones, and the organization is no longer able to access their data, leaving them paralyzed and vulnerable to further breaches.
Demanding ransom
After an organization is locked out of their systems, a ransom is demanded via the ransomware to make organizations pay as quickly as possible. This is normally communicated to the victim via a ransom note, which is either programmed to be set as the display background of the device victims are trying to access their files from, or is contained in each of the encrypted directories so it is found as victims attempt to open their files.
These notes inform the victim of the price they must pay to regain control of their infrastructure, which are often demanded in cryptocurrency. If and when the ransom is paid, the victim receives either the encryption key or a copy of the encryption key that can be entered into the decryptor program (also provided by the attacker), which restores organizational access to the files and data.
These three components make up the framework for any ransomware attack, although their implementation can vary based on threat actor group.
How ransomware attacks
Ransomware comes in many forms, including:
- Encryptors: As the name suggests, encryptors encrypt a system’s data and make it inaccessible to anyone without a decryption key. One of the most common types of ransomware, this damage from encryptor ransomware can be widespread and devastating.
- Doxware/leakware: Doxware or leakware steal confidential information and threaten to make it public if the organization does not pay the ransom. This type of ransomware is often effective because of the panic response it elicits in personnel who do not want their organization’s reputation to be damaged in the wake of an attack.
- Scareware: Scareware is designed to mimic a computer issue, like a virus, and direct victims to a site to pay in order to resolve the problem. Some only use pop-ups on the display screen to flood the screen with alerts, while others actually lock the device so it is inaccessible to personnel.
- Lockers: Lockers do not encrypt individual files within a system, but simply lock users out so they cannot access any of their infrastructure without paying to have it unlocked. This attack often involves a simple display that demands the ransom and may include a timer to encourage faster response from the organization.
- Ransomware-as-a-service: RaaS has become more popular in recent years, and refers to anonymous threat actors that act on behalf of another party to carry out an attack. From infiltrating a system to collecting the ransom, these anonymous hackers receive part of the payment in exchange for their assistance.
Real-life examples of ransomware attacks
WannaCry
The WannaCry ransomware attack of May 2017 affected Microsoft Windows users worldwide, encrypting data and demanding Bitcoin ransom payments. This mass attack targeted organizations around the globe, using EternalBlue, a Microsoft exploit developed by the NSA for older Windows systems. This exploit was stolen by hacker group The Shadow Brokers and subsequently leaked roughly a month before the attack, which allowed for the ransomware’s rapid propagation to a large number of countries across industries.
Related Reading: Linguistic Analysis of WannaCry Ransomware Messages Suggests Chinese-Speaking Authors
Petya
Petya is a strain of ransomware that targets Microsoft systems, encrypting data and preventing the operating system from starting. First observed in March 2016, it demands ransom payments in Bitcoin and was initially propagated via email attachments, although there have since been attacks using Petya malware that use a variety of TTPs to do damage.
One of its most notable variants, dubbed NotPetya, emerged in June 2017 and was used to carry out a widespread ransomware attack around Europe and the US. These attacks primarily targeted Russia and Ukraine, and are believed to be politically-motivated attacks against Ukraine that took place on its Constitution Day.
Bad Rabbit
A suspected variant of Petya, Bad Rabbit ransomware was first observed in 2017 and disguised itself as an Adobe Flash installer, exposing those who unknowingly visited compromised websites via drive-by downloads. Once infected, a victim’s display would demand a Bitcoin ransom payment within 48 hours, although it was reported that payment did unlock the device, which does not always happen during ransomware attacks.
REvil
REvil was a Russian-language RaaS group that executed ransomware attacks by threatening to release sensitive organization information to the public unless a ransom was paid. In one of its most high-profile cases, it obtained confidential schematics for unreleased tech products. An announcement was made in January 2022 by the Russian Federal Security Service that it had dismantled REvil and arrested several of its members.
In one of its most noteworthy attacks, REvil targeted global IT infrastructure provider Kaseya in July 2021 by hacking its Virtual Systems Administrator software, spreading REvil ransomware to its users. The attack affected thousands of organizations, either directly or indirectly, and was carried out by exploiting an unpatched vulnerability that was fixed by Kaseya nine days after the incident took place.
Conti
Conti ransomware, which has existed since 2020, utilizes a number of TTPs to distribute the malware, including spear phishing campaigns, weak RDP credentials, and the exploitation of vulnerabilities in external assets. In February 2022, Conti chats were leaked, identifying individuals involved with the ransomware group and exposing other details of how it is run. However, there is evidence that Conti is still operating despite the leaks, and is still an active threat in the ransomware space.
Related Reading: Conti Affiliate Leaks Ransomware Documents
Colonial Pipeline
Carried out by criminal hacking group DarkSide, a ransomware attack was leveraged against American oil pipeline system Colonial Pipeline in May 2021 that led to the suspension of all pipeline operations in an effort to contain the attack. Working with the FBI, the organization made a payment of 75 bitcoin, approximately $4.4 million, to DarkSide, making it the largest attack on an oil infrastructure target in American history. They were subsequently provided an IT tool by the threat actor group to restore the system. It was announced in June 2021 that 63.7 of the bitcoin, or $2.3 million of the total payment, had been recovered.
Related Reading: DarkSide Ransomware Links to REvil Group Difficult to Dismiss
Kronos
In December 2020 a ransomware attack against workforce management company Ultimate Kronos Group left many organizations, including some major enterprise companies, unable to process payrolls and consequently in violation of their obligations to employees. UKG was subsequently sued by several of its customers for alleged negligence in security practices and data protection, highlighting the importance of organizations implementing best practices to protect their and their users’ data.
Recommended: The Great Cyber Exit: Why the Number of Illicit Marketplaces Is Dwindling
Ransomware trends
As ransomware evolves to become more aggressive to organizations, there are developments that organizations should be aware of to better protect themselves from these types of threats.
Ransomware by the numbers
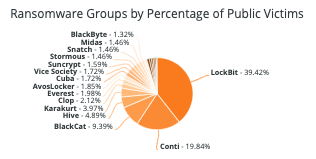
2021 saw an increase in the number of ransomware attacks executed against organizations, growing by 105 percent compared to 2020. Although they make up just a small portion of total victim numbers, governments and healthcare organizations saw particularly steep growth in attacks, with the former seeing a 1,885 percent increase in the number of attacks and the latter experiencing a 755 percent increase. Especially with the rise of remote work, threat actors have taken advantage of heightened vulnerabilities that leave organizations more susceptible to a breach in their infrastructure.
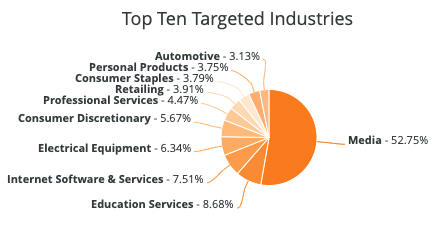
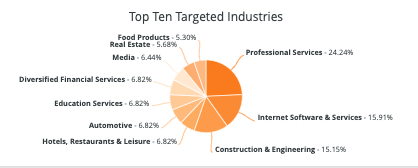
Not only has the quantity of ransomware events proliferated, but ransomware actors have also evolved their tactics to make for more severe attacks that are meant to increase the likelihood of victims sending payment.
Coordinating attacks with major organization events like an IPO, sharing confidential information on victim-shaming sites, and threatening to sell stolen data to outside parties that are willing to pay for it have all been observed by Flashpoint as methods being used to put pressure on companies to submit to ransom demands.
Boards considerations: Ransomware
With ransomware a firmly established part of the threat landscape across sectors, more responsibility is now placed on the board of an organization to ensure that their security teams have a solid plan to prevent and deal with ransomware breaches effectively and legally. As attacks become more severe, several factors are making it even more important for boards to take on an active role in defending their organizations against ransomware.
Ransomware attacks made up 75 percent of claims reported to cyber insurance companies in 2021, marking the rapid growth in both volume of attacks and the demand from organizations to have a safety net to protect their assets in the event of such an attack. This boost has become unsustainable for cyber insurers, leading to some, like AXA, announcing that ransomware attacks will no longer be covered under their policies.
Meanwhile, judicial bodies are tightening the standards organizations are held to to disclose attacks, and limiting the circumstances under which it is legally permissible to pay the ransom. As a result, these changes stand to put companies in an even more difficult position if a ransomware attack does occur, which means prevention must be prioritized over reaction.
Ransomware prevention
As your organization takes steps to strengthen its defense against ransomware attacks, it’s helpful to identify things that make your personnel and infrastructure more susceptible to being targeted by threat actors. This knowledge can assist you in understanding what steps to take to better protect your organization from a successful ransomware attack.
What do threat actors look for to target organizations?
Some of the key weaknesses that are in your control that threat actors look for to make for an easier attack include:
- The use of outdated devices or software, which increase the likelihood of there being exploitable vulnerabilities in your systems that threat actors can gain access through
- Browsers or operating systems that are not patched
- A lack of a proper backup, making the use of malware to encrypt an organization’s file and data more harmful and easier to leverage a ransom payment from
- Cybersecurity awareness and training that has not been prioritized, increasing the chances that an attack will be successful and the organization will not have a coherent defense response
Additionally, there are other elements that may make certain companies more susceptible to ransomware attacks that are not necessarily changeable, but are important to be aware of to emphasize the importance of a strong ransomware prevention and defense plan.
Many companies targeted by ransomware attacks:
- Possess valuable, accessible data that a ransomware actor can steal. This both raises the chances that an organization will pay to retrieve it, and gives the threat actor a backup since it’s more likely that third parties in underground communities would be willing to pay for the stolen data if the organization refuses.
- Are large enough to have the resources to pay a higher ransom fee. Many ransomware actors are motivated by money, which means targets that are in a position to pay more per attack are favorable. The entertainment industry is one of the most-targeted categories because its companies often have the funds and motivation to pay more to regain their stolen files.
- Have more potential for damage. Although financial motivations are often a primary concern in the ransomware space, some threat actors execute these attacks for the purpose of causing widespread harm that amplifies its impact. Supply chain companies are one example of an organization type that has the ability to cause damage to multiple other companies during a single attack, which makes them a bigger target for threat actors.
- Have many remote workers. Since working remotely requires heavier use of softwares and systems that may have vulnerabilities threat actors can take advantage of, organizations that employ more remote workers may be viewed as better targets by ransomware actors looking to exploit infrastructure weaknesses to spread their malware.
Preventing a ransomware attack
With all of these factors in mind, it’s important to have a realistic view on how ransomware risk fits into your organization’s broader threat landscape analysis. Having a strong threat intelligence program in place is a good start to protecting your assets and infrastructure from an attack, but it is only one part of building a good defensive strategy.
A robust cyber awareness training program is one of the most impactful ways you can preempt potential threats. An effective program educates all of your employees about best cybersecurity practices and teaches them how they can contribute to a more secure organization, minimizing the risk of successful ransomware distribution through methods like email phishing. Best practices for individuals include:
- Not clicking on suspicious email attachments or interacting with links that could contain malware
- Not sharing personal information that could assist threat actors in accessing your personal system or device to infiltrate your organization
- Keeping operating systems and applications up to date to take advantage of the latest security patches that help protect your files and device
- Avoiding the use of unknown USB sticks or unverified download sources that could contain malware to infect your device
- Using a VPN when connecting to public WiFi networks
In addition to these steps each employee should take to help prevent a successful breach, there are broader organizational measures that can be enacted to further impede threat actors from executing a successful ransomware attack. These include:
- Having a strong data backup: Since a ransomware attack relies on blocking organizations’ access to their files and data, having a robust backup means that if your original assets are encrypted, you still have access to your infrastructure. It’s important to protect this backup so that it cannot also be encrypted and leveraged against you during an attack.
- Strengthening user authentication and other policies: Exploiting RDP vulnerabilities is one of the most common ways threat actors gain access to devices and data to encrypt. As an organization, requiring employees to have strong passwords and use MFA can prevent the success of these TTPs. It’s also best practice to limit each individual’s data access to only what they actually need to complete their jobs, which minimizes the access a threat actor can get to an organization’s files from any one employee.
- Investing in a robust anti-ransomware program: Using virus scanners and other ways to filter content sent to your employees prevents distribution attempts that are propagated through personnel. It’s also important to consider that some threat actors use other TTPs or well-researched and advanced spear phishing attacks that can be successful against even the most conscientious employees, so it’s crucial to have a backup plan to defend against an attack if malware does infect your organization’s systems. Implementing programs that can detect possible malware behavior and stop the encryption of files before you can no longer access them gives you a safety net if ransomware is distributed to any of your organization’s devices.
- Implementing tabletop exercises and cyber extortion-specific training: Having discussions before an attack to prepare your teams for their role in a potential attack strengthens your response plan and supports involved parties in better executing their parts if an attack does occur. Similarly, company-wide training that educates employees on common threat actor TTPs, like social engineering, helps preemptively combat attacks by lowering the chance that an individual will fall victim to a ransomware actor’s attempts to infiltrate your organization.
- Maintaining an IR playbook: Keeping an updated playbook that contains resources and capabilities of your organization works two-fold to help optimize your response to a ransomware attack. By ensuring you are staying current with your response plan by keeping the playbook updated, and by consistently working to improve your plan and expand its resources, you are better positioning your company and teams to act quickly during an emergency.
Ransomware attack response and recovery
In the event that a ransomware attack does impact your organization, mapping out how to respond quickly and effectively can greatly minimize the damage afterwards. Planning ahead is key, as it saves your entire team valuable time in the moment when it’s most impactful, and ensures that everyone knows how to proceed so all efforts are aligned.
Among the most important aspects to include in your response plan are clear definitions of roles and responsibilities for involved teams and individuals, business continuity plans to minimize an attack’s impact on your customers and users, communication plans, and vendor partnerships.
The basic steps of a ransomware response can usually be broken into the following parts:
Evaluate and isolate
After validating that an attack is taking place, it’s important to determine its scope—how widespread has it become? Understanding this will help you stop it as quickly as possible by taking the affected devices off of organization networks they’re connected to, preventing the ransomware from spreading to shared drives and other devices. It is also best practice to take your backups and other systems offline to prevent the ransomware from infecting them as well.
Assess the damage
After you have secured your organization from further damage, your response teams can begin to investigate the scope of the attack and determine how much of your system has been impacted. Determining the strain of ransomware that was used, what specific files and data have been encrypted, and whether your backups are secure and functioning are also considerations to make as you evaluate the incident.
Execute your response plan
Once you have a clear view of what has been impacted, you can move forward with recovering your data and finding a solution to restore system access to your personnel. In addition to disclosing the attack to all involved parties, possible solutions to consider include:
- Making use of backups, if they sufficiently cover the encrypted data.
- Using a third-party decryptor, if one exists, to decrypt data without dealing with the ransomware attackers.
- Making use of law enforcement and/or a negotiator to deal with the threat actor, potentially paying the ransom if it is deemed legally permissible. Law enforcement can also assist with providing additional resources, further investigation, and potential insights into a threat actor’s TTPs.
It’s important to note that submitting to a ransom demand is not always legal, so it’s crucial to include law enforcement and a knowledgeable party from your own organization to verify that ransom payment is allowed. Since some threat actors are tied to sanctioned entities, or are sanctioned themselves, a due diligence investigation may be needed.
It has historically been in the threat actors’ best interest to follow through on restoring access to your files and data once they receive a payment, since failing to do so can damage their reputation and decrease the likelihood that future victims will pay. However, it should be noted that there have been cases where threat actors do not follow through on their promise to decrypt your data, so paying the ransom should be carefully considered.
Analyze your organization’s security posture
After you have restored access and retrieved your data, your security teams must perform an audit to determine which vulnerabilities were exploited that allowed for a successful ransomware attack and make the necessary changes to prevent it from happening again.
It is not uncommon for the same organization to experience a ransomware attack multiple times, usually because they do not fix the underlying causes of the vulnerabilities, allowing threat actors repeat access. Implementing new and improved measures to secure your infrastructure will make its recovery smoother and more stable.
Secure your organization against ransomware attacks
Your organization’s data, infrastructure, and personnel are valuable—don’t let threat actors take advantage of them. Sign up for a free trial and see firsthand how Flashpoint cybersecurity technology can help your organization access critical information and insight into ransomware actors and their tactics, techniques, and procedures (TTPs).

