Blog
What Is Threat Intelligence?
Understanding the foundations — and impact — of an effective threat intel program

Cyber threat intelligence positions security teams to understand, analyze, and act on important information in order to build up a company’s defense. The quality of your threat intelligence program directly correlates with how effectively your organization is able to protect itself from risks and keep sensitive data secure.
What’s ahead: Key learnings
In this article, we:
- Define threat intelligence and explain why it’s vital to organizations of all sizes and industries
- Give examples of threat intelligence sources that can be used to collect data and inform your organization’s risk remediation and security program
- Provide a list of elements an effective threat intelligence program
Threat intelligence definition
Threat intelligence, which is sometimes referred to as cyber threat intelligence, refers to the information and data (i.e. open source intelligence, or OSINT), and context (i.e. finished intelligence) that can be used to identify, prioritize, and thwart a wide variety of threats that can pose a serious risk to an organization.
These risks include everything from cyber threats like data breaches, vulnerabilities, as well as ransomware and distributed-denial-of-service (DDoS attacks)—and physical threats, like protests, violent extremism, and jihadism—which could endanger an organization’s assets, personnel, stakeholders, customers, partners, and infrastructure. Threat intelligence, which may also refer to the threat intelligence industry, is also an essential decision-making tool for companies seeking to build and extend long-term defense plans to prepare for and mitigate threats.
The importance of strong cyber threat intelligence
Regardless of industry or company size, security breaches and undetected vulnerabilities have the potential to do serious harm to your organization’s assets, customers, personnel, and infrastructure. Threat actors are using increasingly advanced tactics, techniques, and procedures (TTPs) to target a more diverse range of victims for ransomware attacks, data breaches and theft, third-party attacks, and other methods of attack.
Recommended reading: Why the Full Vulnerability Intelligence Picture Depends on Data Beyond CVE/NVD
While having a strong incident response plan is a must-have component of any security team, it is only the tip of the iceberg that makes up defense and protection. The best way to defend your organization is to stop an attack from happening in the first place, which requires strong awareness of the threat landscape as it relates to your company. Threat intelligence covers the entire process, from collecting information to disseminating its insights to other teams. Optimizing each step further prevents successful attempts by threat actors to infiltrate your infrastructure and cause damage.
Cyber threat intel analysts: The security professionals elevating threat intelligence
To effectively gather, analyze, and put threat intelligence into action, cyber threat intelligence analysts should be a critical part of your security posture. They are responsible for creating and executing a plan tailored to your organization’s needs amid an evolving threat landscape—in order to maximize the success of security efforts and proactively call attention to imminent risks that your teams should focus on.
One of the most important qualities analysts bring to the table is an understanding of where to look for information and how trends in the overall cyber threat landscape pertain to your organization’s risk factor. From searching the deep and dark web to evaluating risk apertures specific to your company, they provide the context that is needed for adjacent roles, like threat hunters and CSIRT/CERT to better accomplish their jobs.

Sources of threat intelligence
Threat actors work through many channels, and similarly, threat intelligence can and should be found through a range of sources to give a wider perspective of how your organization may be targeted. The sources your security teams, and specifically your threat intelligence analysts, utilize in their data collection may include:
- Open source intelligence (OSINT): Data and information that is available to the public, though not necessarily only through the surface web. If something is publicly available, it means threat actors have open access to it to leverage for their gain, making it incredibly important to include OSINT in your collections.
- Threat actor groups and illicit communities: Potentially hidden or harder-to-access groups where threat actors communicate information that can be relevant to your organization’s security knowledge. This source is especially important when coupled with threat analysts’ knowledge of specific threat actor TTPs, since that can inform which communities should be most-closely observed according to your organization’s risks.
- Internal information sources: Tools your organization uses to manage its security landscape, including Security Information and Event Management (SIEM) and log tools. These provide a holistic view of historical data and real-time monitoring of security sources to make your threat intelligence more specific to your organization.
- Corporate sharing groups: Organization-led communities that agree to share cybersecurity information. By giving and receiving knowledge to and from companies in your industry, it provides the added benefit of alerting you to potential threats other organizations are watching.
Mapping out a strong threat intelligence program
Any threat intelligence program involves five core lifecycle stages, which describe each step in the journey of collecting and disseminating data.
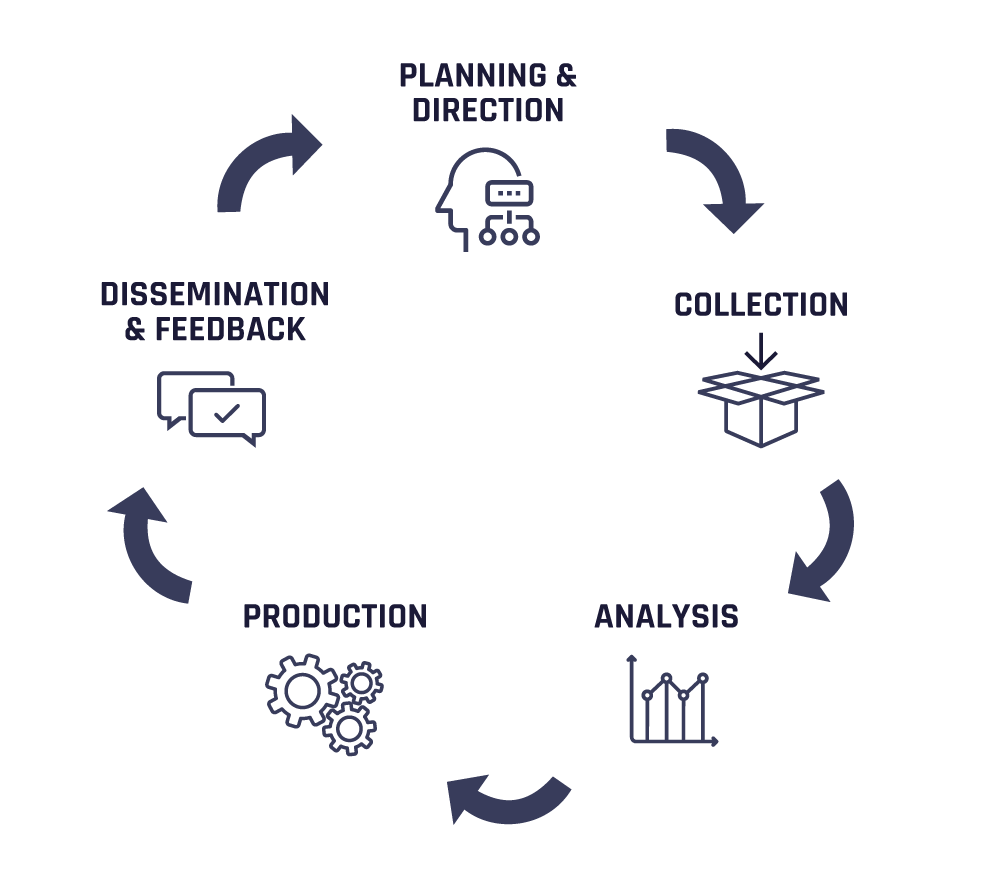
These steps include:
- Planning and direction: Set the scope and objectives for core intel roles and processes.
- Collection: Deploy data gathering and processing techniques and sources.
- Analysis: Translate raw intel into meaningful and taxonomized actors, events, and attributes.
- Production: Assess intel significance and severity based on business and environmental context.
- Dissemination and feedback: Report on finished intel, considering urgency and confidentiality.
While the specific needs of each organization vary, there are common qualities of threat intel programs that every company can aspire to have in order to boost its effectiveness at mitigating risks. Above all, the goal should be to make your teams’ findings actionable and have clear plans in place that outline how to handle any imminent threats that are discovered. While robust data collection is important to build out your full threat landscape, it is significantly less useful if all of your effort goes into gathering information rather than utilizing it to continually build up defense ability.
Get Flashpoint on your team for threat intelligence
Any organization’s security capabilities are only as good as its threat intelligence. Flashpoint’s suite of tools offer you a comprehensive overview of your threat landscape and the ability to proactively address risks and protect your critical data assets. To unlock the power of great threat intelligence, sign up for a demo or get started with a free trial.