Blog
The Threat of Clop Ransomware: How to Stay Safe and Secure [Updated]
Clop is a dangerous form of ransomware that has recently leveraged the GoAnywhere MFT vulnerability and MOVEit zero-day to compromise a large number of organizations

What is Clop ransomware?
Clop (also known as Cl0p) is an extortionist ransomware-type malware that originated in 2019 and operates on the Ransomware-as-a-Service (RaaS) model. Clop is a variant of the CryptoMix ransomware family and since its release, there have been several improved versions of the malware.
Examining the ransomware itself, Clop is a Win32 PE file that is distributed using executables that have been digitally signed by a verified signer—which makes it appear more legitimate, helping it bypass security software detection. Once Clop infiltrates the system, it then attempts to disable Windows Defender and remove the Microsoft Security Essentials.
For the last two years, Clop ransomware has stayed outside the spotlight ever since their high-profile attack on Accellion, which led to the arrest of six of their operators at the hands of the Ukrainian government. However, Clop has made significant impacts on the cyber threat landscape.
Clop leverages MOVEit zero day vulnerability
Clop has found a new vulnerability to exploit—CVE-2023-34362 (VulnDB ID: 322555), the MOVEit vulnerability. Clop had apparently begun exploiting the zero day since May 27, 2023. However, it was not until May 31st that the vulnerability was disclosed by its vendor.
Clop formally claimed responsibility for the recent MOVEit cyberattacks, and the threat actor group asserts that they deleted any stolen data belonging to governments, the military, and children’s hospitals. Clop has also stated to have compromised hundreds of organizations but the exact number of victims is unknown.
MOVEit victims have until June 14, 2023, to pay ransoms or else they will be listed on Clop’s data leak site:
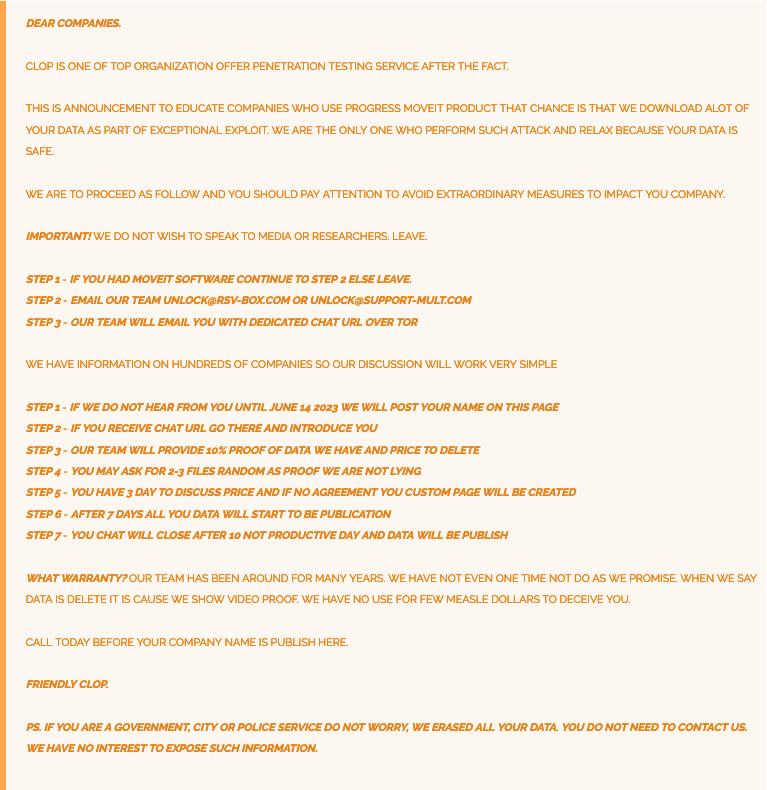
Flashpoint is currently monitoring the situation for new developments. The following is a timeline, as well as several resources to aid in the identification, prevention, and general education of this latest cyberattack:
- May 27, 2023: Clop begins exploiting the MOVEit zero-day vulnerability. Although breaching multiple organizations, the group did not immediately extort victims.
- May 31, 2023: Progress Software Corporation publicly discloses the MOVEit vulnerability.
- June 1, 2023: Flashpoint adds MOVEit Transfer (DMZ) Unspecified SQL Injection to VulnDB (ID: 322555).
- June 2, 2023: The MOVEit vulnerability is assigned CVE-2023-34362.
- June 4, 2023: Microsoft attributes MOVEit attacks to Clop, who they refer to as “Lace Tempest.”
- June 5, 2023: Clop confirms that it is responsible for the MOVEit Transfer data-theft attacks and Zellis, a payroll and HR solution provider, confirms to have been compromised.
- June 6, 2023: Multiple organizations associated with Zellis, such as BBC and British Airways confirm that they have been compromised by the MOVEit vulnerability.
- June 7, 2023: CISA releases a joint Cybersecurity Advisory detailing Clop’s exploitation of the MOVEit vulnerability.
Clop uses GoAnywhere MFT vulnerability for ransomware attack
Flashpoint observed significant increases in Clop’s activity, with the ransomware group claiming more than 650 victims (as of August 9) posted on their ransomware blog.
This newfound success has been the result of exploiting a flaw in Fortra’s file-sharing solution GoAnywhere MFT (managed file transfer). Known as CVE-2023-0669, the GoAnywhere MFT vulnerability is a remote code execution (RCE) that potentially permits a remote attacker to execute arbitrary commands with a specially crafted request in the command console.
Leveraging the GoAnywhere MFT vulnerability, Clop had initially claimed to have compromised 130 companies, and had steadily released the names of their victims through their ransomware blog. As of August 9, the number of victims, including affected third parties has grown to over 650. This figure stems from the Clop ransomware blog, in addition to data from Flashpoint’s data breach intelligence database Cyber Risk Analytics (CRA).
How to detect and prevent Clop ransomware
Given Clop’s new tactic of exploiting the GoAnywhere MFT vulnerability, the best way to prevent a potential data extortion event is to patch the vulnerability—information regarding the latest patch (7.1.2), in addition to comprehensive metadata can be found in VulnDB. Remediating CVE-2023-0669 is critical since threat actors and illicit communities are actively discussing how to scan for susceptible systems given Clop’s success with the vulnerability.
However, the GoAnywhere MFT vulnerability is not the only weapon in Clop’s digital arsenal. The ransomware group has been known to leverage DDoS and various phishing tactics in previous attacks. As such, organizations will need to ensure that they are following best practices and implementing proper security controls. Organizations can do the following to help prevent a data extortion event:
- Updating outdated devices and software using comprehensive vulnerability intelligence.
- Prioritizing critical vulnerabilities known to be used in other ransomware attacks using tools such as VulnDB’s Ransomware Likelihood Prediction Model.
- Frequently review administrator users, or accounts with high privilege levels while auditing admin logs for unusual activity.
- Ensuring that the organization has proper cybersecurity training so that employees can identify and report suspicious email attachments and malicious links.
Prevent and respond to a ransomware attack with Flashpoint
Ransomware response is equally as important as prevention. In the event that an organization is impacted by ransomware, having a well-practiced incident response plan can greatly minimize damages. To learn more about how Flashpoint empowers security teams to prevent and respond to ransomware attacks, contact us, or sign up for a free trial.