Blog
The Five Phases of the Threat Intelligence Lifecycle
The threat intelligence lifecycle is a fundamental framework for all fraud, physical, and cybersecurity programs—whether mature and sophisticated in their operations, or merely aspiring
What Is the Threat Intelligence Lifecycle?
The threat intelligence lifecycle is a fundamental framework for all fraud, physical, and cybersecurity programs—whether mature and sophisticated in their operations, or merely aspiring.
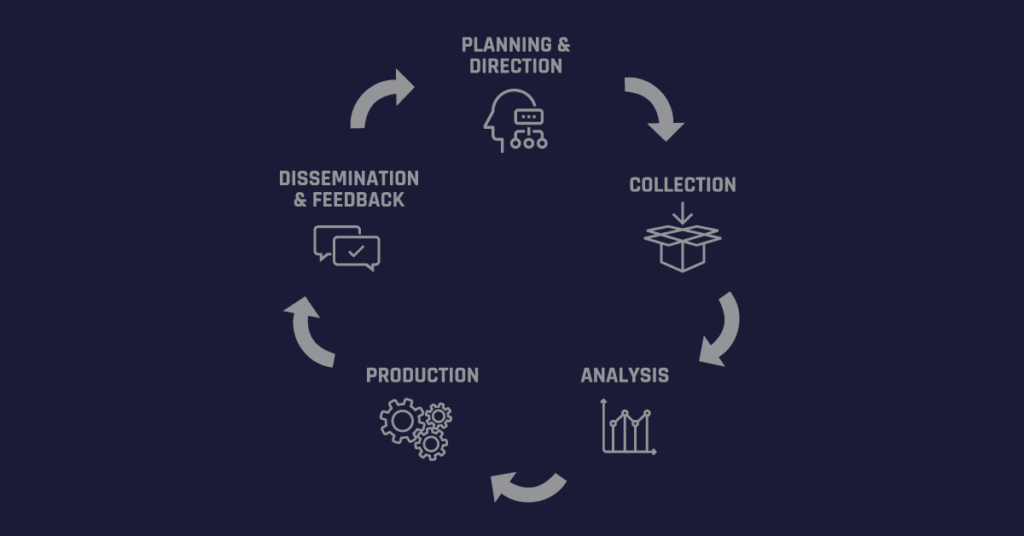
At a high level, the threat intelligence lifecycle outlines the core steps to apply and uphold high standards of data hygiene necessary to confidently draw conclusions and take action based on the data. This iterative and adaptable methodology contains five phases that ultimately convert raw data into finished intelligence (see Figure 1).
Figure 1: The Five Phases of the Threat Intelligence Lifecycle
Key Objectives at Each Phase of the Threat Intelligence Lifecycle
- Planning and direction: Set the scope and objectives for core intel roles and processes.
- Collection: Deploy data gathering and processing techniques and sources.
- Analysis: Translate raw intel into meaningful and taxonomized actors, events, and attributes.
- Production: Assess intel significance and severity based on business and environmental context.
- Dissemination and feedback: Report on finished intel, considering urgency and confidentiality.
PHASE 1: Planning and Direction
Phase one of the threat intelligence lifecycle is arguably the most important stage not because it’s first, but because it sets the purpose and scope of all following intelligence activities. As an initial step, lay out the main goals and tasks for your threat intelligence program, which are often referred to as intelligence requirements (IRs). For public sector organizations, they’re also commonly called essential elements of information (EEIs).
IRs should reflect the core objectives of the team and the value that finished intelligence will ultimately deliver (e.g., Operational efficiency gains, mitigated risk, and faster detection and response).
This may start to sound like you’re preparing a business case, and that’s a good thing. The better you define and quantify your intelligence goals, the easier it is to establish and track key performance indicators (KPIs) and to demonstrate success.
For more concrete examples, see how Forrester calculated a 482% ROI for organizations leveraging Flashpoint’s threat intelligence platform.
In many cases, senior leadership—such as the Chief Information Security Officer (i.e., the CISO or CSO)—will guide planning and direction at this stage and establish the core program goals and challenges, along with all potent external threats.
Key Considerations in Phase 1
— Which types of assets, processes, and personnel are at risk?
— How will threat intelligence improve operational efficiency for my team?
— What other systems and applications could benefit?
PHASE 2: Collection and Processing
Data quantity and quality are both crucial aspects of the threat intelligence collection stage. If you veer astray with either quantity or quality, your organization could be inundated with false positives or you miss serious threat events.
Intelligence collection establishes the scope of your sources, both in terms of the data volume and type. This includes a wide range of threat types like phishing, compromised credentials, network logs, common vulnerabilities and exploit (CVEs), leaked malware variants, and far more malicious activity generated by threat actors.
The processing component of phase two then seeks to normalize, structure, and deduplicate all of the amassed data. Specific processing procedures often include reducing the volume of raw data, translating conversations obtained from foreign-language dark web marketplaces and illicit forums, and metadata extraction from malware samples.
Key Considerations in Phase 2
— Where are your current internal and external blindspots?
— What technical and automated collection techniques can you employ?
— How well can you infiltrate cybercriminal forums and closed sources on the dark web?
Related reading: Applying the Threat Intelligence Lifecycle for Physical Security
PHASE 3: Analysis
The analysis phase is a largely qualitative and often human-oriented process aimed. It is aimed at contextualizing processed threat intelligence through the enrichment and application of known structural data or advanced correlation and data modeling.
As artificial intelligence and machine learning continue to mature, some human-oriented tasks, such as mundane, low-risk decisions, will increasingly become automated. This will free up operational resources and staff to prioritize more strategic tasks and investigations.
Key Considerations in Phase 3
— Which types of assets, processes, and personnel are at risk?
— How will threat intelligence improve operational efficiency for my team?
— What other systems and applications could benefit?
PHASE 4: Production
Once the threat intelligence analysis is complete, phase four transitions into development efforts that focus on arranging finished intelligence into easy-to-digest graphical charts, dashboards, and reports. During production, it’s essential to identify the most meaningful information and derive logical conclusions from the data and analysis completed in the prior phase.
Recommendations that outline appropriate courses of action will often include prepared decision trees and procedures to initiate incident and ransomware response, threat remediation, and patch management, among many others.
Based on the finished intelligence, production stakeholders finalize reports and prepare the communications to final team members and key decision makers. Ultimately, this final audience of the finished threat intelligence will assess the analysis and decide whether or not to take action.
Key Considerations in Phase 4
— What are the most important findings of the analysis, and what’s the best way to illustrate them?
— With what degree of confidence is the analysis reliable, relevant, and accurate?
— Are there clear and concrete recommendations or next steps regarding the end analysis?
PHASE 5: Dissemination and Feedback
In order to drive results and address the risks, fraud and security teams must distribute their finished intelligence reports to the appropriate stakeholders. These teams may run the entire gamut: dedicated fraud teams; cyber threat intelligence (CTI) teams; security operations (SecOps) teams; vulnerability management teams; third-party risk teams; and the senior leadership teams responsible for resource allocation and strategic planning.
Upon receiving the finished intelligence, stakeholders evaluate the findings, make key decisions, and provide feedback to continually refine intelligence operations. Improvements in this operational domain tend to focus on the speed and efficiency of intelligence activities and the time to reach final delivery.
Key Considerations in Phase 5
— Which stakeholders benefit from finished threat intelligence reporting?
— What is the best way to present the intelligence and at what delivery frequency?
— Ultimately, how valuable is the finished intelligence? How actionable is it, and does it enable your organization to make informed security decisions?
— And, finally, how can you improve on it going forward—both in terms of finished intelligence and ameliorating your organization’s intelligence cycle?
See Flashpoint Intelligence in Action
Sign up for your risk-free 90-day trial and see how Flashpoint can provide you with the actionable threat intelligence you and your entire team need to identify and respond to threats targeting your organization. When equipped with Flashpoint Intelligence, you move a step ahead of threat actors and the cybercriminals impacting your business and bottom line.
