Blog
Risk Intelligence Index: Cyber Threat Landscape by the Numbers
Flashpoint’s monthly look at the cyber risk ecosystem affecting organizations around the world, including intelligence, news, data, and analysis about ransomware, vulnerabilities, insider threats, and takedowns of illicit forums and shops.
Ransomware
Flashpoint’s latest ransomware infographic paints a sobering picture of the evolving threat landscape, as cybercriminals employ increasingly sophisticated—and effective—tactics. Last month, our analysts observed a total of 397 ransomware attacks.
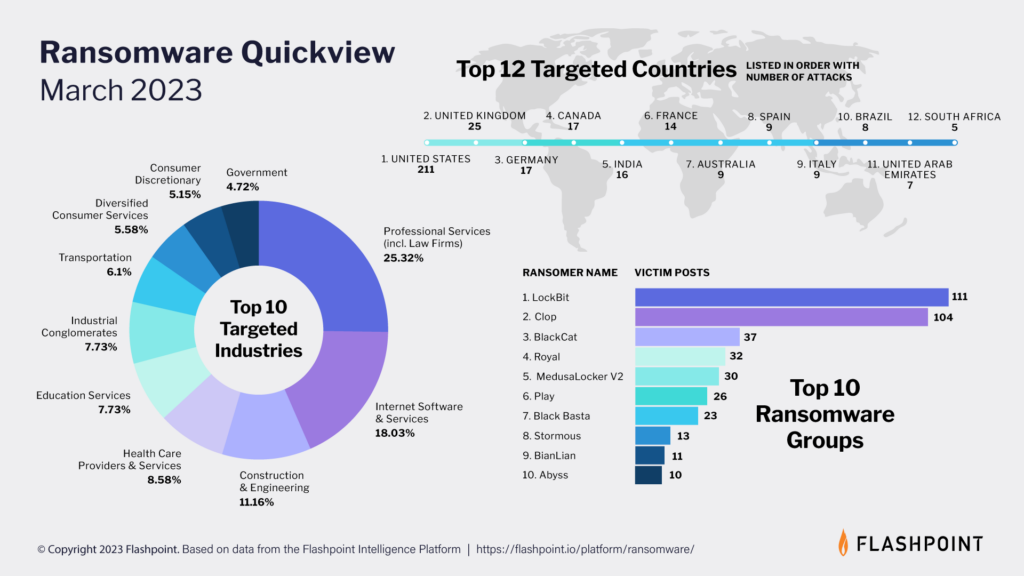
Key takeaways for the state of ransomware
- Organizations in the United States bore the brunt of ransomware attacks, accounting for a staggering 211 incidents—a 66 percent increase compared to last month.
- The top three industries targeted by ransomware were Professional Services, Internet Software & Services, and Construction & Engineering.
- Clop ransomware has emerged as one of the most active ransomware groups, securing the second spot in March’s top 10 ranking. Last month, Clop garnered attention by exploiting a remote code execution vulnerability—allegedly enabling them to acquire data from over 100 organizations, although they only disclosed a few victim names on their blog.
Vulnerabilities
According to our intelligence, 2,245 new vulnerabilities were reported in March, with 379 of them being missed by the Common Vulnerabilities and Exposures (CVE) and National Vulnerability Database (NVD).
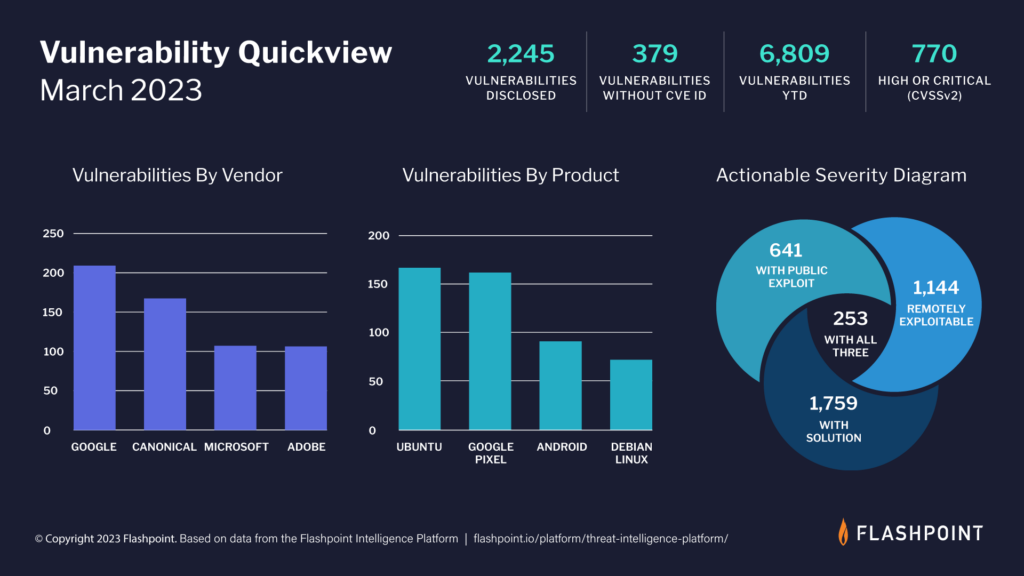
Key takeaways for the state of vulnerability intelligence
- Approximately 34 percent of March’s disclosed vulnerabilities are rated as high-to-critical in severity, which if exploited, could pose a significant risk to an organization’s security posture.
- Over 78 percent of March’s vulnerabilities are remotely exploitable, meaning that if threat actors are able to leverage these issues, they can execute malicious code no matter where the device is located.
- Nearly 29 percent of March’s vulnerabilities already have a documented public exploit, which drastically lessens the difficulty to exploit.
- Vulnerability Management teams can potentially lessen workloads by nearly 88 percent by first focusing on actionable, high severity vulnerabilities—i.e., vulnerabilities that are remotely exploitable, that have a public exploit, and a viable solution; 253 of March’s vulnerabilities meet this criteria.
Insider Threat
The tactic of recruiting insiders has become immensely popular amongst threat actors aiming to breach systems and/or commit ransomware attacks.
In March, our analysts collected 5,586 posts advertising insider services—both from threat actors seeking insiders and malicious employees offering their services. Of those, 1,127 were unique posts from individuals in illicit and underground communities.
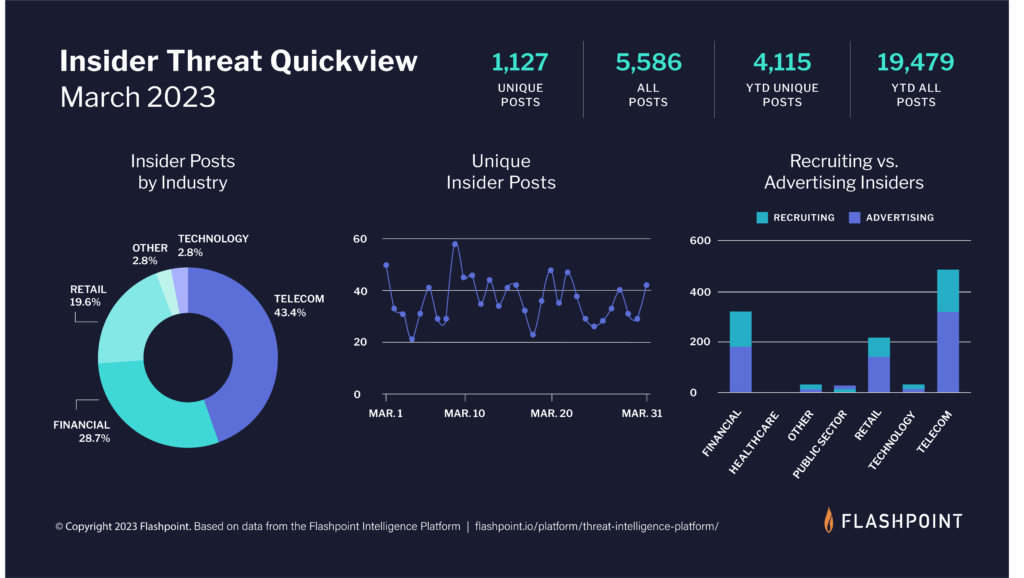
Key takeaways for the state of insider threat intelligence
- In March, Flashpoint tracked 5,586 posts related to insider threats activity—both from threat actors attempting to solicit insider-facilitated access and from disgruntled employees offering their services. Of the total, 1,127 were unique postings.
- At this time, the Telecom industry is the most targeted sector, followed by Financial and Retail.
- Looking into the state of insider threats further, Flashpoint found that the majority of insider threat related postings originated from inside the organization with malicious insiders offering their services. Most of this activity came from the Telecom sector.
Takedowns
In March 2023, there were numerous takedowns, voluntary shutdowns, and arrests affecting ransomware, markets, account shops, card shops, and individual cybercriminals. Here are the high-profile takedowns.
Breach Forums
On March 21, 2023, mid-tier hacking forum Breach Forums was shut down following the arrest of its administrator, Conor Brian Fitzpatrick (aka “pompompurin”), six days prior.
Read the court doc here.
Worldwiredlabs
On March 3, a US Magistrate Judge issued a seizure warrant for Worldwiredlabs[.]com, a domain used by cybercriminals to sell malware, including remote access trojan (RAT) “NetWire,” which is capable of targeting and infecting major computer operating systems.
On March 7, an international law enforcement effort led to the seizure of Worldwiredlabs. The FBI had begun its investigation in 2020, and uncovered that it was the only known online distributor of NetWire.
Read the court doc here.
Get best-in-class intel
The following data is derived from the Flashpoint Intelligence Platform and VulnDB, the most comprehensive and timely source of vulnerability intelligence available. Sign up for a free trial today.