Blog
Risk Intelligence Index: The April 2023 Cyber Threat Landscape
Flashpoint’s monthly look at the cyber risk ecosystem affecting organizations around the world, including intelligence, news, data, and analysis about ransomware, vulnerabilities, and insider threats.
Ransomware
Flashpoint’s latest ransomware infographic paints a sobering picture of the evolving threat landscape, with cybercriminals employing increasingly sophisticated tactics. Last month, our analysts observed a total of 411 ransomware attacks.
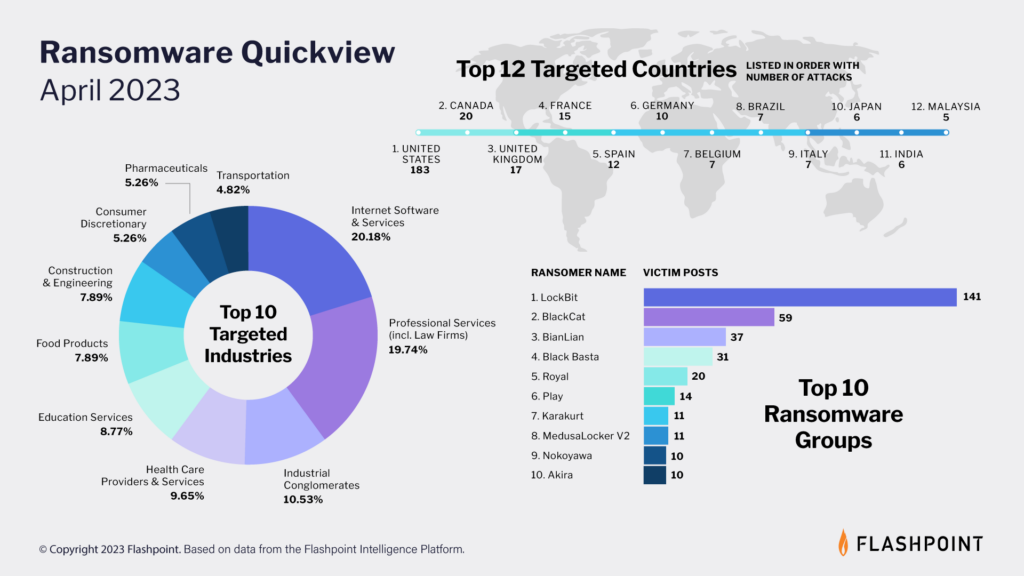
Key takeaways for the state of ransomware
- Organizations in the United States bore the brunt of ransomware attacks, accounting for a staggering 183 incidents.
- The top three industries targeted by ransomware were Internet & Software Services, Professional Services, and Industrial Conglomerates.
Vulnerabilities
According to Flashpoint, 1,689 new vulnerabilities were reported in April, with 267 of them being missed by the Common Vulnerabilities and Exposures (CVE) and National Vulnerability Database (NVD).
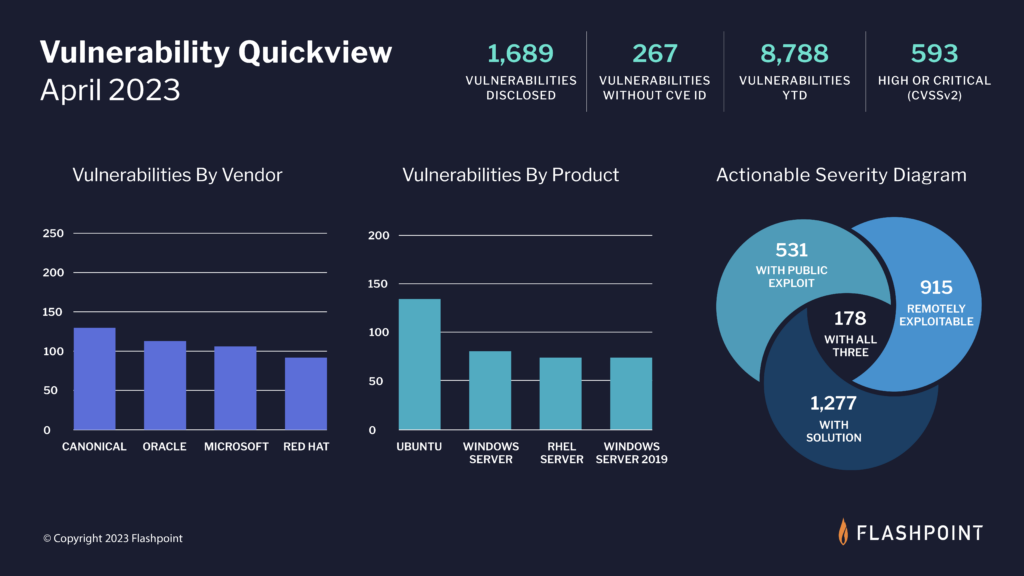
Key takeaways for the state of vulnerability intelligence
- Approximately 35 percent of April’s disclosed vulnerabilities are rated as high-to-critical in severity, which if exploited, could pose a significant risk to an organization’s security posture.
- Over 54 percent of April’s vulnerabilities are remotely exploitable, meaning that if threat actors are able to leverage these issues, they can execute malicious code no matter where the device is located.
- Nearly 31 percent of April’s vulnerabilities already have a documented public exploit, which drastically lessens the difficulty to exploit.
- Vulnerability Management teams can potentially lessen workloads by nearly 89 percent by first focusing on actionable, high severity vulnerabilities—vulnerabilities that are remotely exploitable, that have a public exploit, and a viable solution—178 of April’s vulnerabilities meet this criteria.
Insider Threat
The tactic of recruiting insiders has become immensely popular amongst threat actors aiming to breach systems and/or commit ransomware attacks.
In April, our analysts collected 13,710 posts advertising insider services—both from threat actors seeking insiders and malicious employees offering their services. Of those, 1,399 were unique posts from individuals in illicit and underground communities.
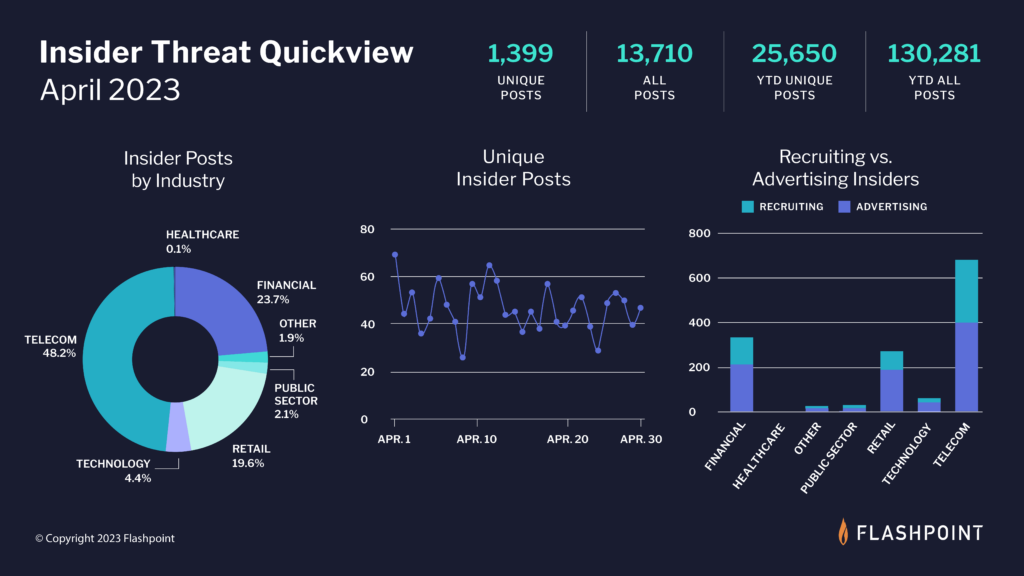
Key takeaways for the state of insider threat intelligence
- In April, Flashpoint tracked 13,710 posts related to insider threat activity—both from threat actors attempting to solicit insider-facilitated access and from disgruntled employees offering their services. Of the total, 1,399 were unique postings.
- At this time, the Telecom industry is the most targeted sector, followed by Financial and the Retail Sector.
- Looking into the state of insider threats further, Flashpoint found that the majority of insider threat related postings originated from insiders advertising their access to outside threat actors. Most of this activity came from the Telecom sector.
Takedowns: Genesis Market
On April 5, the FBI announced its seizure of the illicit market Genesis Market and arrested 119 individuals associated with the cybercriminal market.
Genesis Market facilitated the sale of stolen credentials, including browser credentials, login information, passwords, and cookies since 2018. These listings were often harvested from a victim’s device through commoditized credential-stealing malware.
During its operation, Genesis was considered among the most popular and high-quality bot shops, alongside Russian Market and 2easy. Despite its seizure, Genesis Market support claimed that the darknet website is still operational and that it was working on setting up new surface web mirrors.
Analysis
Compromised credentials pose a significant risk to corporations and individuals, and Genesis Market’s takedown will likely prompt market vendors and buyers to find another replacement market. Genesis Market was unique because it offered fully integrated fingerprint creation technology and self-updating logs—services currently unavailable through Russian Market and 2easy—the remaining, most popular bot shops. In the absence of a similar service, any remaining market operators will likely attempt to create a similar market in the future.
Get best-in-class intel
The following data is derived from the Flashpoint Intelligence Platform and VulnDB. Sign up for a free trial today.