Blog
China is Exploiting Network Providers and Devices, Says US Cybersecurity Advisory

On June 7, the US Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), and National Security Agency (NSA) released an advisory outlining the different tactics, techniques, and procedures (TTPs), particularly common vulnerabilities and exploits (CVEs), that Chinese state-sponsored cyber-enabled actors are utilizing to attack and exploit entities and individuals abroad. The CVEs are associated with network devices.
The advisory details how threat actors target telecommunications providers’ Remote Authentication Dial-In User Service (RADIUS) servers, which can be manipulated using SQL commands in order to ultimately dump usernames and passwords.
The advisory mentions some components of the home-office technology suites where risks may be heightened.
- Chinese threat actors have been targeting small office or home office network devices and attached storage devices. Flashpoint analysts note that home office configurations may have become a more attractive target, as enterprise employees and technology are now distributed over multiple work-from-home nodes.
- Virtual private networks (VPN) and public-facing applications are being targeted.
- Compromised servers serve as “hop points” for malicious actors to register emails, host command and control (C2) servers, and access victim networks.
The advisory also explains how malicious actors pivot and adjust their tactics based on observations of network defender accounts and following the release of information regarding campaigns. They use publicly available scanning tools to identify critical users in an infrastructure, and blend custom tools with living-off-the-land techniques to hide their activities.
What vendors are Chinese state-sponsored groups targeting?
The following vendors have been targeted by Chinese hackers since 2020. All 16 vulnerabilities mentioned in the advisory can be triggered remotely, which highlights the appeal to target these vulnerable systems:
| Vendors | CVE ID | VulnDB ID |
| Cisco | CVE-2018-0171 | 177622 |
| CVE-2019-15271 | 217100 | |
| CVE-2019-1652 | 197222 | |
| Citrix | CVE-2019-19781 | 219857 |
| DrayTek | CVE-2020-8515 | 222650 |
| D-Link | CVE-2019-16920 | 214372 |
| Fortinet | CVE-2018-13382 | 201634 |
| MikroTik | CVE-2018-14847 | 185977 |
| Netgear | CVE-2017-6862 | 158172 |
| Pulse | CVE-2019-11510 | 203753 |
| CVE-2021-22893 | 254549 | |
| QNAP | CVE-2019-7192 | 214036 |
| CVE-2019-7913 | 214037 | |
| CVE-2019-7914 | 214038 | |
| CVE-2019-7915 | 214039 | |
| Zyxel | CVE-2020-29583 | 245511 |
Flashpoint has also reviewed these vendors further to reveal how many of their products are affected by these issues. These products should be prioritized for patch management due to their known targeting by highly skilled state-sponsored actors:
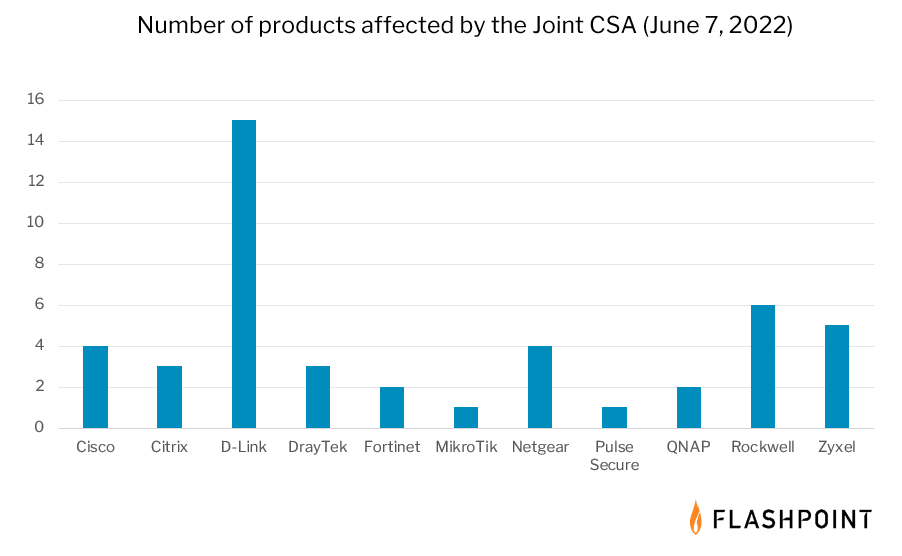
Managing patches will be difficult without quality vulnerability intelligence
To best protect themselves, the Joint CSA advises that organizations patch these CVEs immediately.
However, it is not that simple.
For the vulnerability affecting D-Link (CVE-2019-16920), all affected products have reached end-of-life (EOL) meaning that this issue will never be fixed. Organizations should pay particular attention to EOL software and make sure that these systems are upgraded or replaced.
Aside from that, security teams should prioritize fixing the other 15 vulnerabilities above, but remediating only those issues may not be enough.
If an organization is deploying any of these affected products, it is likely that there are even more vulnerabilities affecting them—including vulnerabilities without CVE IDs that were not addressed in the Joint CSA. As such, vulnerability managers need to research all known issues affecting vulnerable assets, focusing on those with publicly available exploits. Prioritization should then consider factors like attack location and threat likelihood to determine which vulnerabilities should be remediated first.

Taking a closer look at affected products
To illustrate this, consider CVE-2019-1652. This vulnerability affects Cisco’s RV320 and RV325 routers, but it is not the only exploitable issue. A closer look using the VulnDB database shows that both products have a total of 72 vulnerabilities affecting them, with seven of them having documented exploits. And of those, six are remotely exploitable. Therefore, addressing only CVE-2019-1652 may not be enough.
Continuing this practice, Citrix ADC, the product identified in CVE-2019-19781, has a total of 107 vulnerabilities affecting it—with five of them not reported by CVE/NVD; three of those have proof-of-concepts. But aside from the issues missed by CVE, 12 have public exploits. The other affected Citrix product, Citrix Gateway, has 105 known vulnerabilities, with 16 of them having known exploits. One has no CVE ID.
Conducting this kind of research for each affected product will require time, however it may be a necessary action for organizations seeking visible improvements in their security posture. Doing so will give security teams deeper visibility into their risk apertures.
The need for comprehensive vulnerability intelligence
Thorough research is critical for minimizing actual risk, but some organizations may not be able to perform that kind of detailed vulnerability analysis. Most security practitioners are aware that CVE/NVD often misses exploit details, solution information, as well as other vulnerability metadata, which often forces them to scour outside sources for actionable details. But most importantly, CVE/NVD also fails to report over 94,000 known vulnerabilities.
Threat actors and illicit communities will take advantage of any weakness and that includes vulnerabilities without CVE IDs. And if your vulnerability management program is unaware of nearly 33 percent of all known vulnerabilities, there is a real chance that some assets will continuously be at-risk.
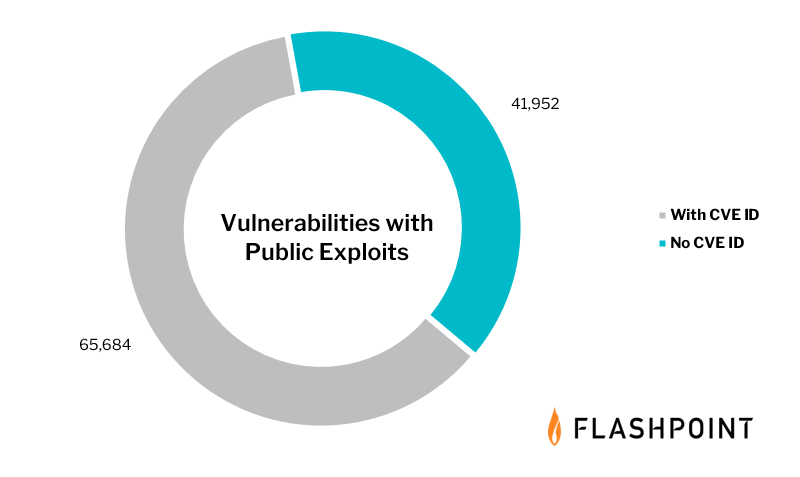
The total number of known vulnerabilities with a publicly available exploit is 107,636 and if we limited it to only those with CVE IDs, that number would drop to 65,684.
If an organization did somehow remediate every exploitable issue contained in CVE, they would only have reduced their exposure by only 61 percent.
Enhancing your defense capabilities with threat intelligence
Combining vulnerability intelligence with threat intelligence can greatly enhance an organization’s ability to reduce risk. Chatter from actors on Chinese-based web forums, chat services, and marketplaces has brought major contributions to the threat landscape.
For example, exploits and some zero-day vulnerabilities used in China’s Tianfu Cup were found to be used offensively in later attacks. In addition, the Log4j vulnerability “Log4Shell” was originally discovered by researchers at Alibaba, and that issue continues to cause problems for organizations. As such, a view into online communities can enhance a network defenders’ ability to maintain strong defensive postures.
Reveal vulnerabilities and remediate them faster with Flashpoint
If your goal is to proactively manage risk, you will need a quality vulnerability intelligence feed. VulnDB is the most comprehensive, detailed, and timely source of vulnerability intelligence, covering over 290,000 vulnerabilities affecting thousands of vendors and products. Sign up for a free trial to gain visibility into all known exploitable issues, including those missed by CVE/NVD.