GLOSSARY
The Practitioner’s Guide to Vulnerability Intelligence
Security practitioners need comprehensive vulnerability intelligence to focus on the issues that matter most. However, the intelligence that many organizations rely on is likely incomplete. Find out if your current VI vendor is causing you to spend more time validating vulnerabilities rather than managing them.

What’s ahead
In this article we…
1. Define what vulnerability intelligence is, and how it informs vulnerability management;
2. Describe the vulnerability intelligence lifecycle and how it works;
3. Explain the importance of vulnerability intelligence, and how your organization can gain access to a comprehensive source
What is vulnerability intelligence?
Vulnerability intelligence is a specific form of threat intelligence focused on the aggregation or dissemination of information about computer vulnerabilities that may put organizations at risk.
The number of software is growing exponentially. As such, so too are the number of vulnerabilities. A vulnerability is a flaw in computer software or hardware that allows an attacker to cross privilege boundaries. By taking advantage of flaws contained in products, threat actors can infiltrate an organization’s system, stealing sensitive data or causing damage to the network.
As such, organizations need a comprehensive source of vulnerability intelligence so that they can better prioritize and remediate risk.
The difference between “good” vs. “bad” vulnerability intelligence
Your vulnerability management program is completely dependent on the quality of your vulnerability intelligence. This makes it important to know what separates good intelligence from bad.
Depending who you ask, the definition of vulnerability intelligence could change. Some may lump together vulnerability intelligence and vulnerability management concepts together. Some may even consider CVE and NVD as a comprehensive source of vulnerability intelligence.
There are distinctions between comprehensive and lacking sources of vulnerability intelligence. Although the industry, as well as some practitioners believe that the Common Vulnerabilities and Exposures (CVE) and the National Vulnerability Database (NVD) are the go-to resources for disclosed vulnerabilities, this is far from the truth.
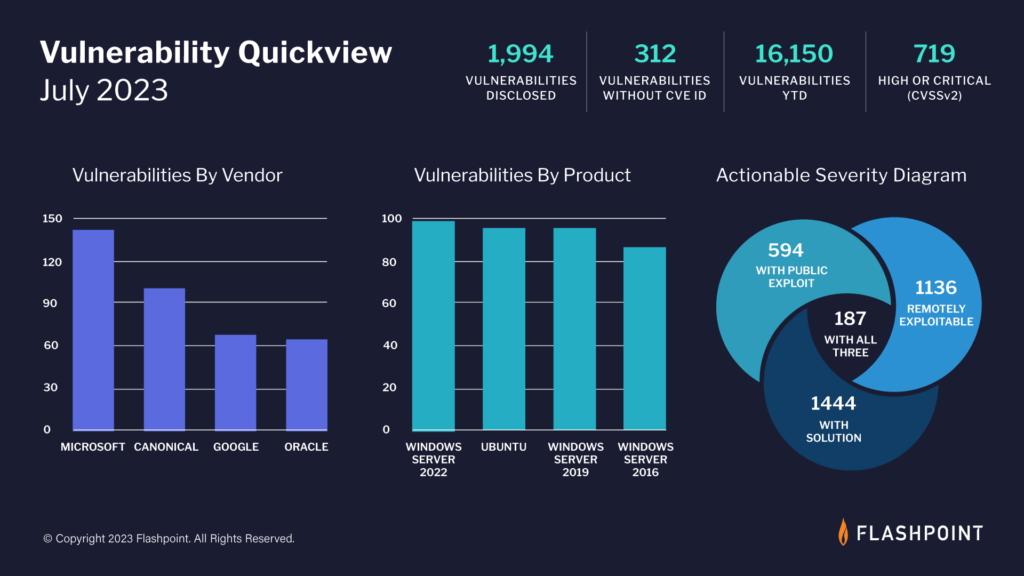
As seen in Flashpoint’s Cyber Threat Intelligence Index, CVE and NVD consistently fail to report hundreds of vulnerabilities every month. Over time, this adds up, with CVE / NVD missing over 99,500 known disclosed vulnerabilities. This means that organizations strictly relying on CVE may be completely unaware of almost a third of known vulnerability risk.
Understanding the vulnerability intelligence lifecycle
To understand what creates this intelligence gap, it is essential to understand the vulnerability intelligence lifecycle. If the vulnerability intelligence powering your Vulnerability Management program is incomplete, your organization is at a greater risk of being compromised. And in order to decipher whether your organization is using an incomplete source, it is important to know the elements of vulnerability intelligence.
Vulnerability intelligence breaks down into three key functions:
- Vulnerability discovery
- Vulnerability research
- Vulnerability analysis
What is vulnerability discovery?
Vulnerability discovery is the process of researching a piece of computer software or hardware to evaluate for the presence of vulnerabilities. As an organization, you can only analyze the vulnerabilities you are aware of. It is impossible to mitigate or remediate risk that you never knew existed.
Vulnerability discovery is the first step in the vulnerability intelligence lifecycle, and it is the most important—since this is the foundation that will dictate the effectiveness of your vulnerability risk program.
This state is where researchers discover and publish vulnerabilities so that vulnerability databases (VDBs) can then aggregate and build upon those disclosures. It is vital that the vulnerability intelligence you rely on is aware that there are thousands of unique channels out there and actually monitors them.
The vulnerability discovery process breaks down further into two steps:
- Vulnerability sources
- Vulnerability monitoring
Vulnerability sources
The more vulnerability sources you can identify, the more robust your vulnerability coverage becomes. Vulnerabilities are disclosed and published in a wide variety of mediums, including mail lists, blogs, service sites like GitHub, websites catering to exploit disclosures, and more.
Vulnerability disclosures are published across social media, the deep web, researcher blogs, product bug trackers, code commits, and more. Since there is no single source, it is vital that organizations intelligently aggregate as many vulnerabilities as they can so they can know which to focus on.
Vulnerability monitoring
In the scope of vulnerability intelligence, vulnerability monitoring is the act of keeping tabs on a wide variety of sources that produce vulnerability disclosures. This process includes identifying new disclosures, determining if information is valid, normalizing the data, adding metadata, and then including it into the vulnerability feed. Mature vulnerability intelligence solutions then offer support for the data they aggregate to ensure an organization understands, and can better utilize that data.
This is a real challenge. Adding to the difficulty is that a single source can sometimes contain thousands of disclosed vulnerabilities. What sources, and how many are you aware of and actively monitoring?
What is vulnerability research?
Vulnerability research is the process of researching vulnerabilities to determine if any of them affects your organization’s systems.
While monitoring vulnerability sources, you must research the vulnerabilities that appear and determine if any affects your organization’s systems. Does a vulnerability affect a vendor in your supply chain, or a product used by your organization? If it does, what versions of that product are also susceptible to that vulnerability? Is an exploit available? Can you install a patch or upgrade to remediate it?
This function is not so simple as vulnerability research can have different meanings and occur at different times depending on the role of the person performing it. The roles that can influence this are:
- Vulnerability researchers
- Vulnerability intelligence companies
- Security analysts at organizations
For a vulnerability researcher, it includes doing the initial examination and investigation into a piece of computer software or hardware that contains bugs that may allow for privileges that weren’t intended. Examples include Flashpoint’s own vulnerability research team that has discovered and published vulnerabilities affecting the Honey and Bitwarden browser extensions as well as other widely used products.
For a vulnerability intelligence company, the term means the act of going through publicly disclosed vulnerabilities to determine if they are legitimate issues (or classifying them as NAV), aggregating that data, and then normalizing it for consumption by other organizations.
Organizations face a unique problem during vulnerability research. As an analyst, the term may mean researching if disclosed vulnerabilities impact their assets and what risk is posed. This means that your vulnerability research functions depend on the comprehensiveness of what researchers and vulnerability intelligence companies do.
According to that definition, vulnerability intelligence companies should be doing more than just aggregating CVE data—they are also responsible for determining if issues are legitimate and enhancing it with rich metadata. But if you think back to the last vulnerability you researched, how detailed was it?
What is vulnerability analysis?
Vulnerability analysis is the last function of the vulnerability intelligence lifecycle. In this state, you gauge the potential damage a vulnerability can cause if exploited. Ultimately, you are asking yourself, “now that I know this affects me, how bad can it be?”
To better understand overall and potential risk, you need vulnerability metadata, severity information, and impact data.
Vulnerability metadata
By definition, metadata is “a set of data that describes and gives information about other data.” For vulnerabilities, metadata may include the location of the attacker, the attack type, the high-level impact, availability of a solution, status of an exploit, aspects of the disclosure, general types of technology represented, authentication requirements, and more.
Severity
The vulnerability severity refers to how serious, or how big of a risk is associated with it. Low severity issues may not be prioritized as they are not seen to pose much risk to an organization, while high severity vulnerabilities are typically triaged and patched immediately.
Impact
When a vulnerability is exploited, it will impact a system in some manner that may or may not be noticeable to administrators or users. At the highest level, confidentiality may be partially or fully impacted, for example. Impacting integrity can mean a variety of things so it may be described via simple metadata (e.g. the CIA triad) and with verbose descriptions that precisely lay out what happens if exploited.
Why is vulnerability intelligence important?
In our State of Cyber Threat Intelligence report, we stated that hacking was the number one cause for data breaches—accounting for over 60 percent of all reported compromise events. By taking advantage of flaws, hackers can gain a foothold into organizations, creating chaos that can result in extreme financial loss. For this reason, having quality vulnerability intelligence is critical in order to achieve an efficient vulnerability management program.
Knowing vulnerability details is important for determining the potential scope of damage, however, key metadata is often missing from most publicly accessible vulnerability entries and databases.
Unfortunately, many vulnerability intelligence vendors focus solely on collecting issues, but perform little to no quality checks, resulting in inaccuracies and invalid entries. This results in most security teams not being able to spend their time on analyzing vulnerabilities. Instead, they are forced to spend more time validating entries and finding vulnerability metadata themselves.
What should vuln intel provide you?
Vulnerability intelligence should be comprehensive, detailed, and timely. Organizations need to be aware of everything that is in the vulnerability disclosure landscape and have all the details so that they can manage risk as soon as possible. But do they have that kind of visibility using CVE and NVD?
Just because the public source may not have those details, it doesn’t mean that the information cannot be found. If your vulnerability intelligence feed consistently omits important metadata, it’s likely that your intelligence provider is substituting vulnerability intelligence with CVE and NVD.
“We wanted to devote our scarce resources in actually doing something instead of just rating CVSS scores for vulnerabilities. Just knowing we have VulnDB inspires confidence. When you are exposed to it you know that this is quality information.”
Stéphane Grundschober, Vulnerability Manager at Swisscom
Gain access to comprehensive vulnerability intelligence with Flashpoint
Hopefully this guide has been helpful in showing you what vulnerability intelligence is, and why every organization needs it. However, if you’ve begun realizing the shortcomings of your current intelligence vendor, you probably have more questions.
What’s next? What does “good” vulnerability intelligence actually look like? Can I see it for myself? Check out the following resources to learn more:
- Everything You Need to Know About Vulnerability Management
- VulnDB: What comprehensive vulnerability intelligence looks like
- Datasheet: Why VulnDB?
- Case study: Swisscom Frees Up Limited Resources with Better Data
- Case study: VulnDB Enables Continuous Product Security for Dräger
- Free trial: Request free access to VulnDB
Get the latest news and insights delivered to your inbox.
Interested to see top news from Flashpoint hit your inbox directly? Subscribe to our newsletter to receive curated content on a regular basis.