Platform > Ignite > cyber threat intelligence
Flashpoint Cyber Threat Intelligence
Stay ahead of potential targeted threats like cybercrime, emerging malware, ransomware, and hacktivism using Flashpoint Cyber Threat Intelligence (CTI).
Flashpoint CTI delivers tailored and comprehensive intelligence across the deep, dark and surface web to help analysts focus on threats that matter, make smarter decisions and protect their people, places and assets.

Focus on the threats that matter
Don’t spend all of your time sourcing and sifting through disparate sources of threat intelligence. Quickly assess your risk exposure with our finished intelligence, collections, and dashboards. We layer our intelligence with personalized context to help you identify risks that are unique to your organization. Whether you’re deep in investigative work or consuming reports to stay on top of trends, Flashpoint CTI helps you scale your operations and stay ahead of the changing threat landscape.
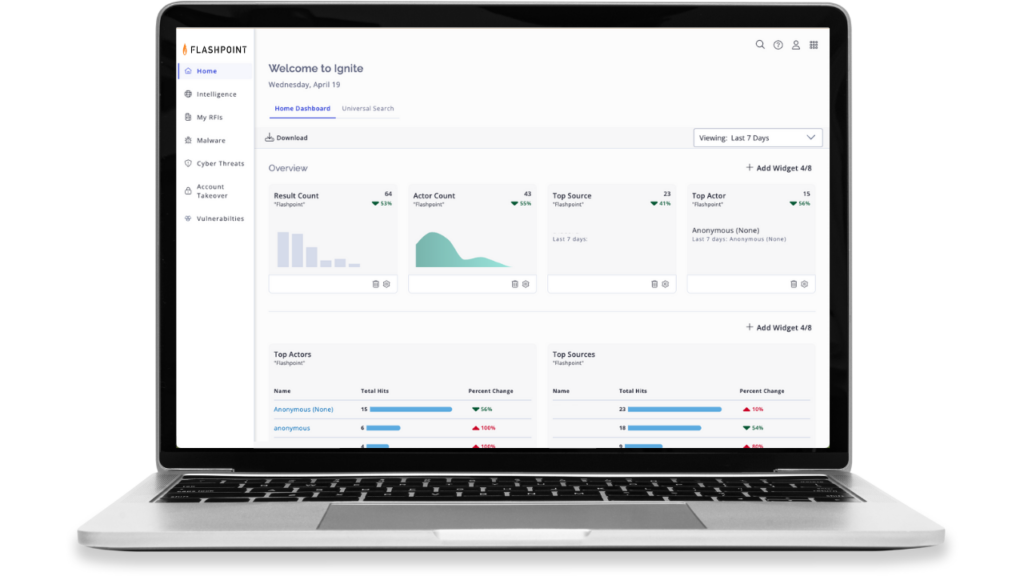
Find valuable conversations, context, and answers fast
Quickly search across our intelligence and collections to help you narrow your investigations and hone in on relevant communities, marketplaces, images, and more.
Effective and actionable threat response
Mitigate the impact of a threat by sharing information with the right teams at the right time to improve the incident response life cycle.
Better decision making
Make faster and more accurate security decisions by evaluating and prioritizing threats and risks using threat intelligence.
Accessible intelligence through AI-conversations
Unlock the power of intelligence through natural, effortless conversations with Ignite AI. Easily converse with our intelligence using AI and recieve instant responses using our finished intelligence.
Fast understanding of a threat actor’s digital identity
An immediate and comprehensive profile of a threat actor’s activities and behaviors, including what they talk about, where they interact, and how they’ve changed over time.
Helping you solve the most critical cyber challenges
Understand how threat actors operate
Quickly learn the most used tactics, techniques and procedures (TTPs) used against your organization and similar organizations to prevent potential targeted attacks.
Stop ransomware attacks before extortion
See the early signs of a ransomware attack and keep tabs on trends from community chatter, IOCs, and threat actor TTPs.
Monitor employee credentials and confidential information
Search and monitor our collections for compromised enterprise accounts and passwords to prevent bad actors from accessing and exploiting confidential information.
Gain full visibility into vulnerabilities
Arm security teams across your organization with the contextual intelligence needed to effectively identify, prioritize, and remediate the vulnerabilities most likely to have an impact on your business.
Flashpoint offerings for Cyber Threat Intelligence
“I sleep a lot better knowing Flashpoint is covering the deep, dark and surface web for us.”
–Global Security team at a technology manufacturer and retailer