Blog
Threat Actors Leverage “Phonecord” Bot to Harass Victims
Although the majority of cyber threat actors are fueled by the desire for financial or political gain, some actors lack traditional motivations altogether. Often referred to as “attention-seekers”, these actors’ malicious activities are driven typically by nothing more than a desire to attract attention by causing chaos for their own amusement. Despite their reputation for nonsensical campaigns, erratic targeting, and low technical sophistication, attention-seekers’ schemes can yield anything from mild nuisances to economic or even psychological distress. In fact, Flashpoint analysts recently observed groups of attention-seekers launch a series of vicious attacks that subject victims to an age-old and universally-despised form of abuse: telephone harassment.
Although the majority of cyber threat actors are fueled by the desire for financial or political gain, some actors lack traditional motivations altogether. Often referred to as “attention-seekers”, these actors’ malicious activities are driven typically by nothing more than a desire to attract attention by causing chaos for their own amusement. Despite their reputation for nonsensical campaigns, erratic targeting, and low technical sophistication, attention-seekers’ schemes can yield anything from mild nuisances to economic or even psychological distress. In fact, Flashpoint analysts recently observed groups of attention-seekers launch a series of vicious attacks that subject victims to an age-old and universally-despised form of abuse: telephone harassment.
Since this particular form of telephone harassment first emerged in late April 2017, groups of attention-seeking actors have harassed a wide range of individuals and organizations via a telephone bot known as “Phonecord”. Although telephone bots in and of themselves are nothing new, Phonecord is relatively unique because it utilizes the social and communication application Discord, which enables users to make international calls directly and easily from the app’s voice chat functionality. And because those seeking to use the Phonecord bot have the option to pay for the service in Bitcoin, most users remain relatively anonymous. While Discord has long been popular among the gaming community, the app’s ease of use and ability to withstand distributed denial-of-service (DDoS) attacks has given rise to its heavy usage among cyber threat actor communities.
Thus far, victims of Phonecord harassment schemes include:
• United Kingdom National Crime Agency (NCA)
• Federal Bureau of Investigation (FBI)
• Various popular pizza chain restaurants
• Hotels
• Individuals whose personally identifiable information (PII) has been exposed previously
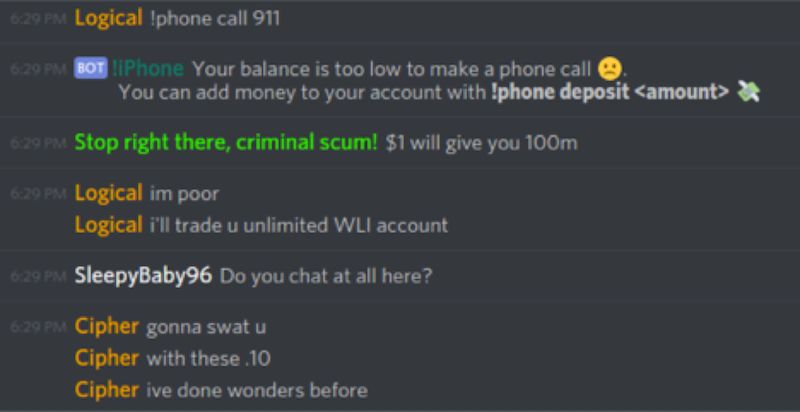
Many of these victims have been harassed in a manner that resembles a common tactic known as “Swatting”, which occurs when a threat actor makes numerous “prank calls” to emergency services in an attempt to dispatch a large number of law enforcement officers to a specific address. Indeed, Flashpoint analysts observed various threat actors utilize Phonecord in similar yet more lighthearted manner: rather than dispatch emergency services, they ordered a large number of pizzas from multiple restaurants to be delivered to the same address. Not only does this leave the unsuspecting victim with an unusually large amount of pizza, it burdens them with the high cost of paying for such pizzas upon delivery. While these types of schemes yield no financial reward for the threat actors involved, they do satisfy these actors’ cravings for attention and amusement at the cost of victims’ discomfort.
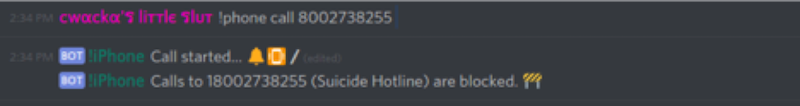
In fact, multiple threat actors have even been known to utilize the Phonecord bot to harass certain individuals and law enforcement agencies on repeat occasions. Unfortunately for many threat actors, their multiple attempts to call numbers including “911”, the suicide hotline, and other emergency services hotlines were unsuccessful because Phonecord’s configuration blocks calls to such numbers.
Assessment & Mitigation
One administrator of the Phonecord bot service most notably took credit for a DDoS attack that took down servers for the popular game Minecraft for an extended period in June 2014. Although this actor and the other administrators have not advertised Phonecord explicitly as a criminal service, numerous instances of abuse have evidently become present.
Flashpoint analysts assess with high confidence that threat actors will likely continue to use the Phonecord bot to carry out harassment campaigns against various individuals and organizations unless the administrators of the service institute additional controls and countermeasures.
The most effective way to avoid becoming the victim of Phonecord and other telephone bot harassment schemes is to exercise extreme caution in safeguarding personal information such as telephone numbers and home addresses. For those whose personal information has already been exposed, taking additional measures by changing telephone numbers and opting to use a P.O. box as opposed to a residential address on all correspondence will serve as additional barriers that may help deter the efforts of some actors.
Victims of telephone bot harassment and/or other malicious schemes are encouraged to report such incidents to the Internet Crime Complaint Center: https://www.ic3.gov/default.aspx