Blog
Recent CISA KEV Additions Include Silent Fixes and Unpatched Vulnerabilities
Flashpoint’s analysis of three new additions to CISA’s KEV catalog that affect ManageEngine, GLPI, and ApacheSpark

KEY TAKEAWAYs
Flashpoint discovered that the root cause for CVE-2022-28810 affects a file named htmLawedTest.php in a third-party library. While a fixed version is available to GLPI users, the root cause may affect other applications that use the htmLawed library prior to 1.2.9.
At the time of publishing, Flashpoint finds that Apache Spark version 3.1.3 is still vulnerable to CVE-2022-33891, despite the vendor listing that version as fixed.
Understanding the latest vulnerabilities added to CISA’s KEV
Since the introduction of the Known Exploited Vulnerabilities Catalog in 2021, the KEV has been an important resource for Vulnerability Management teams—providing much needed visibility into issues that are highly exploitable, as well as vulnerabilities being actively used by Advanced Persistent Threats. On March 7, 2023, CISA added the following vulnerabilities, affecting these products to the KEV:
- Zoho Manage Engine (CVE-2022-28810)
- GLPI (CVE-2022-35914)
- Apache Spark (CVE-2022-33891)
The Flashpoint Vulnerability Research team carefully analyzes vulnerabilities, including those that are included in CISA’s Known Exploited Vulnerabilities Catalog (KEV)—ensuring that every vulnerability contained in VulnDB is of the highest quality.
Of these three vulnerabilities, Flashpoint has observed two major discrepancies with CVE-2022-35914 and CVE-2022-33891. Security teams need to be aware that despite following vendor instructions, certain organizations may still be at risk due to the root causes of each vulnerability.
ManageEngine (VulnDB 287359 / CVE-2022-28810)
CVE-2022-28810 refers to a remote command execution vulnerability in ManageEngine ADSelfService Plus. This allows authenticated remote attackers to gain access to the underlying operating system and may subsequently enable lateral movement within the infrastructure. However, exploitation requires having administrator privileges, which limits how prevalent exploitation of this issue will be. It most likely will be exploited in combination with a misconfiguration or other vulnerabilities that grant privileged access to the system. As a result, we only did a cursory analysis of this one and instead focused on the other two vulnerabilities.
GLPI (VulnDB 301271 / CVE-2022-35914)
CISA lists the affected product as GLPI, however, the CVE description and the vendor’s security advisory both point to a file named htmLawedTest.php in a third-party library. The product in question is called htmLawed and is a PHP library to “purify and filter HTML”. Reading the publicly available exploits, it becomes clear that GLPI is affected as the htmLawedTest.php script is included in the web server path and is remotely accessible.
Beside a token and a session value that need to be extracted from a first request to the script, attackers only need to send a command via the ‘text’ parameter and set the ‘hhook’ parameter to ‘exec’ to exploit the vulnerability.
According to the documentation, the htmLawedTest.php script functions as a “demo web-page” to test the actual library that is implemented in htmLawed.php. htmLawedTest.php itself does not invoke any command execution functions, but we can see that it passes input from the ‘text’ parameter to htmLawed().
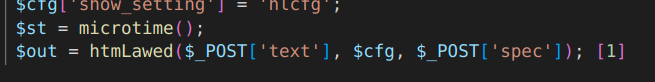
Looking at the main library in htmLawed.php, we can see that the input – now handled as variable ‘$t’ – is used in a variable function call using the variable ‘$C[‘hook’]’.
This variable is part of the configuration argument and the exact data passed to htmLawed() from the htmLawedTest.php script.
The foreach loop iterates through the POST parameter array and adds keys and values to the ‘$cfg’ array if the parameter starts with the character ‘h’. This means that by controlling the ‘hhook’ and ‘text’ POST parameters, an attacker can execute arbitrary PHP functions with an arbitrary argument.
The fixing commit in GLPI shows that htmLawed was updated from version 1.2.6 to 1.2.9, suggesting that the issue is fixed in this version. By downloading and comparing the source code of the releases, we located the fix in htmLawedTest.php.
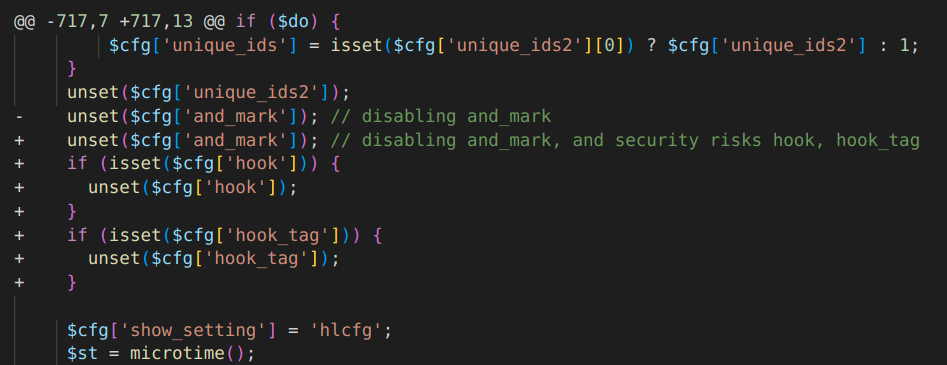
If any POST parameter has set the ‘hook’ or ‘hook_tag’ keys in the ‘$cfg’ array, it is cleared via unset() to prevent invoking arbitrary PHP functions via POST requests.
Interestingly, the vendor was aware about “security risks” of passing this input to htmLawed(), but the changelog for version 1.2.9 does not suggest that any vulnerabilities were addressed. It is unclear whether the vendor was not aware of the ramifications or decided to silently fix it. Flashpoint recommends updating htmLawed to the latest available version and removing the htmLawedTest.php script from production environments.
Apache Spark (VulnDB 295745 / CVE-2022-33891)
CVE-2022-33891 was disclosed on the Apache Spark security page and the oss-sec mailing list as a “shell command injection vulnerability via Spark UI” on July 17, 2022. If ACLs are enabled via the ‘spark.acls.enable’ configuration option, certain input can be passed via the ‘HttpSecurityFilter’ component to a permission check function, which insecurely builds a Unix shell command.
The corresponding Jira issue SPARK-38992 points to multiple pull requests on GitHub, which reveal the root cause of the vulnerability.
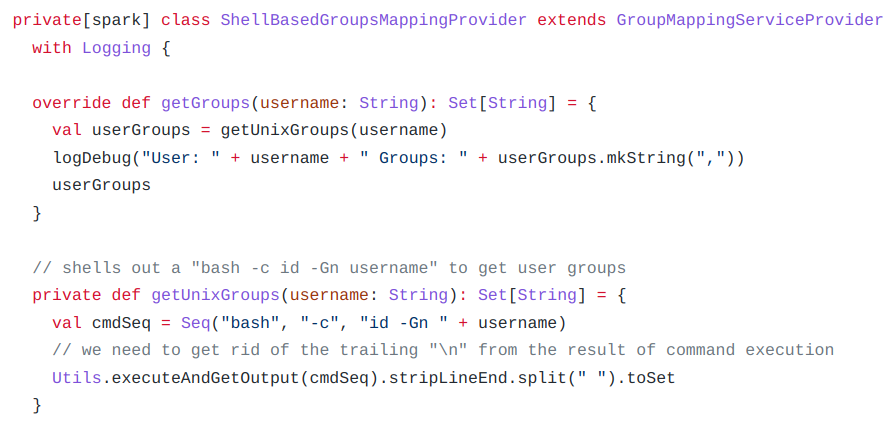
The affected function is reached via the ‘HttpSecurityFilter’ component and according to published exploit code, it requires sending a request to an affected instance with the ‘doAs’ parameter containing e.g. a command enclosed with backtick characters, which are used for command substitution in bash.
In the ‘HttpSecurityFilter’ class, we see that the ‘doAs’ parameter from a request is passed to the securityMgr.checkAdminPermissions() function. This is exactly the permission check for impersonation that the vendor description refers to.
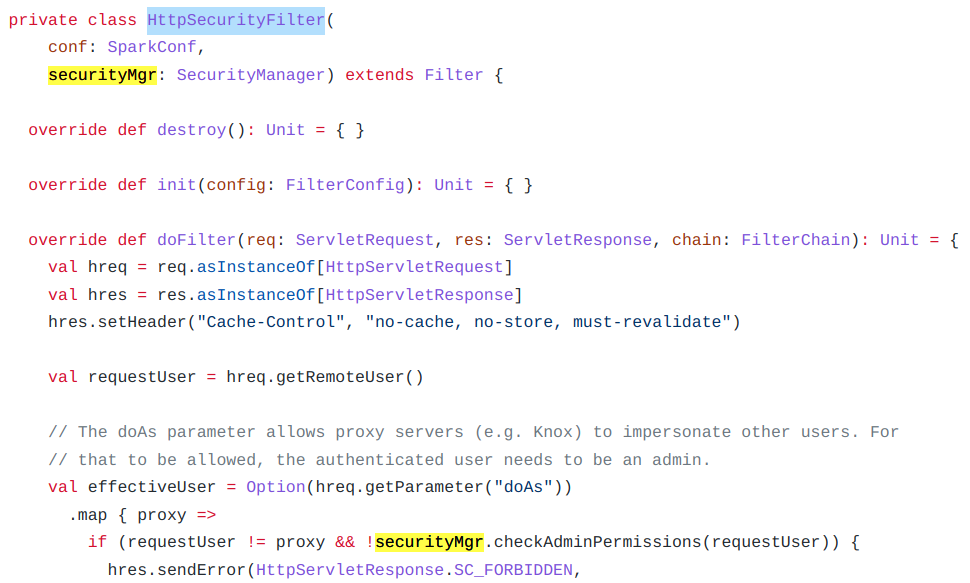
The SecurityManager::checkAdminPermissions() function calls SecurityManager::isUserInACL(), which passes the input to Utils.getCurrentUserGroups().
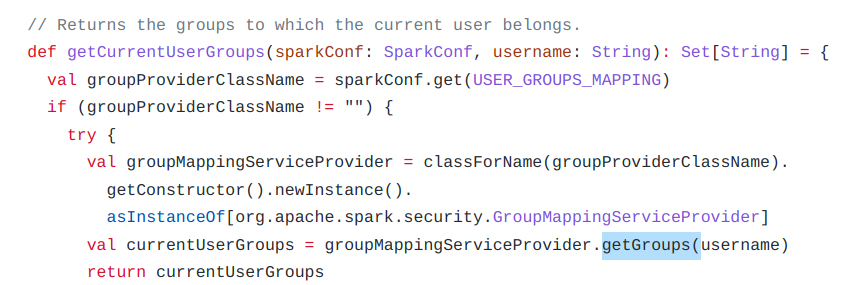
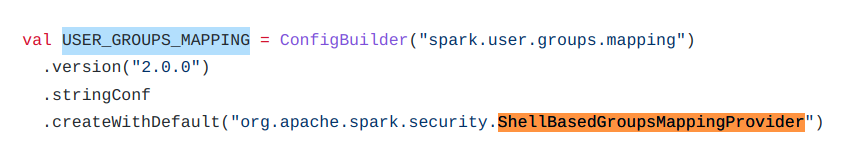
Utils.getCurrentUserGroups() gets the name of the configured group provider (USER_GROUPS_MAPPING), creates an instance of that class and calls the getGroups() method with the still unsanitized request data.
This describes the code path from the ‘doAs’ request parameter to the vulnerable function.
According to the vendor, the issue is fixed in versions 3.1.3, 3.2.2, and 3.3.0. Flashpoint confirms that versions 3.2.2 and 3.3.0 in the GitHub repository include the referenced fix. However, the fix is not included in version 3.1.3. Analyzing the code path, we can see that none of the other functions perform any sanitization in version 3.1.3 either.
Deploying Apache Spark 3.1.3 using Docker, Flashpoint was able to confirm that this version is still vulnerable to the remote command injection vulnerability.
What you need to know
While users of GLPI may have updated to a fixed version to address CVE-2022-35914, the root cause may affect other applications that use the htmLawed library prior to 1.2.9. Since the vendor did not include a security notification in the changelog, htmLawed users may not be aware of the risks for their applications. We strongly recommend updating to the latest version 1.2.11, which also addresses a cross-site scripting issue (VulnDB 314470).
The root cause analysis for CVE-2022-33891 not only allowed us to point to the exact location of the vulnerability but also outlined the path of the request data. This revealed that version 3.1.3 – while listed as fixed by the vendor—is still vulnerable.
Learn more about vulnerabilities with Flashpoint
CISA’s KEV does provide important information about vulnerabilities, however, but it is critical to fully understand each vulnerability and the potential impact. Scenarios like this happen frequently in the vulnerability disclosure landscape, demonstrating the need for comprehensive vulnerability intelligence. Sign up for a free trial to get a deeper understanding of the 313,000 known vulnerabilities—including over 97,000 missing from CVE and NVD.