Blog
2021 Intel Wrap-Up: Insider Threats and Trends—What the Data Tells Us
The following is part of Flashpoint’s 2021 Intel Wrap-Up series, which is based on our data collections and expert analyst research. The following insider threat awareness report is based on data from January 1 – November 31.

The following is part of Flashpoint’s 2021 Intel Wrap-Up series, which is based on our data collections and expert analyst research. The following insider threat awareness report is based on data from January 1 – November 31.
By the numbers: Insider threats
- Flashpoint observed 12,455 total instances of insider recruiting, insider advertising, or general discussions involving insider-related threat activity across 703 open, closed, and invite-only channels.
- 3,450 of these posts are unique and authored by 1,566 threat actors.
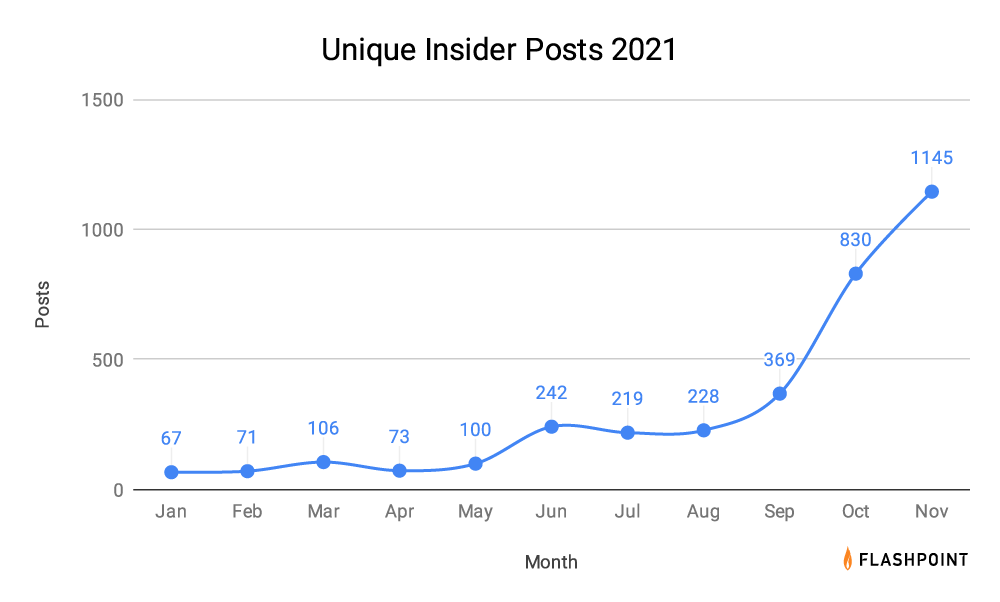
- The sharp increase (seen above) in unique posts from September through November is largely due to low-credibility threat actors attempting to scam those willing to pay for access to an insider. Notably, it has become more difficult to gauge the credibility of an insider post due to the proliferation of scammers.
Insider threat industry breakdown: Where threat actors sought insiders
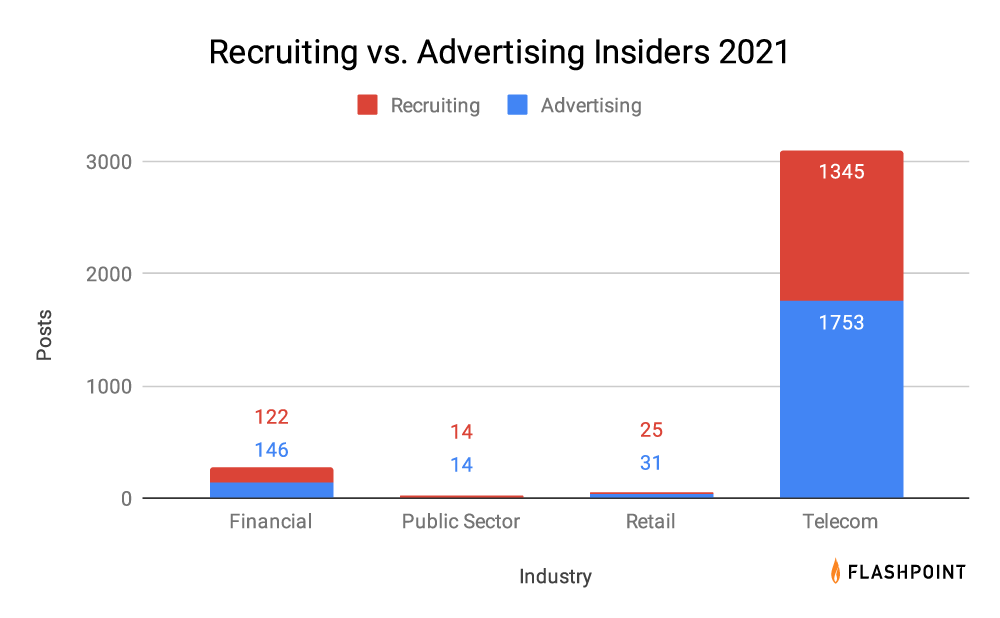
- A majority (89.8%) of threat actors advertised or sought to recruit insiders working at mobile telecommunications providers, with a focus on conducting fraud operations.
- Other industries where insiders were recruited involved the usual suspects: retail, public sector (law enforcement and governments), and the financial sector.
The increasing credibility gap
- Tactics, techniques, and procedures (TTPs) for insider threats are consistent with those observed in years prior. However, one complicating factor is the aforementioned increase in online noise from low-credibility scammers, which increases noise on threat actor channels such as closed chat services.
- The most frequent media attachments within insider posts in 2021 are commonplace: SIM cards, SMS messages, and video demos. However, posts with these media attachments are likely less legitimate because they reuse the same media as many other posts; credible threat actors do not repost the same media or use other threat actors’ media as proof. Furthermore, they do not actually contain information that would verify the threat actor’s credibility.
Related reading: The Insider Threat Intelligence Cycle
Recruiting TTPs
- Threat actors typically have two primary options for recruiting insiders: work with someone they know in the physical world (typically a friend, relative, or colleague), or can set up a digital relationship with someone by recruiting them online.
Known insiders
- Threat actors working with insiders they know in the physical world likely have higher levels of trust, based on both a prior relationship and a mutual fear of repercussions, since each person’s identity is known to the other.
- On that note, a disadvantage of working with a known insider is that if one person is caught, their co-conspirators are also likely to be identified.
Insiders recruited online
- Threat actors who recruit online have more difficulty confirming the credibility and trustworthiness of potential partners.
- However, the talent pool is much broader online and the range of possible targets is exponentially larger.
- It is also less likely that the threat actor will be identified if their insider connection is caught.
Related reading: Demystifying Insider Threat
Insider TTPs
- Insiders commonly post messages within open, closed, and invite-only chat services advertising themselves as insiders and declaring themselves ready to work on various schemes for a fixed price or share of the profits. (Typically, prices are not posted up front.)
- Insider threat actors conduct their attacks in a multitude of ways, and it is difficult to generalize about their initial access methods. Broadly speaking, insider threats gain initial access by leveraging their position in the enterprise to gain access to a protected system, or leveraging their experience to circumvent security controls. Insiders are able to capitalize on their access within the company to collect others’ credentials, hijack their computers, and steal documents to further their malicious campaigns.
- Insider posts observed in these communities focus on account takeover (ATO) activities where an insider facilitates the account transfer and an outside party provides the target. Telecommunication insiders are valuable because they can facilitate SIM swapping attacks that allow attackers to bypass two-factor authentication and conduct account takeovers on targets where they do not have an insider.
Implement an effective ITP with Flashpoint
Insider threat programs (ITPs) require extensive resources in order to operate effectively. Flashpoint provides insider threat teams with extensive visibility into the illicit online communities frequented by insider threat actors; threat actors seeking to recruit insiders at targeted organizations in order to carry out criminal schemes; and threat actors seeking to monetize proprietary data obtained from these schemes. Sign up for a demo or free trial today, and learn how Flashpoint can tailor its offerings to your organization’s unique ITP needs, challenges, and objectives.