Solutions > BY THREATS AND RISKS > Ransomware and data extortion
Ransomware and data extortion
Ransomware remains one of the most impactful threats to organizations today, offering attackers a lucrative opportunity to make money off of your valuable assets and data. This can be done through data encryption, data extortion, and in some cases both (known as double extortion). Given the increased likelihood of encountering these threats, it is critical to understand them, prevent them, and have a clear plan for response in case of being a victim.

Ransomware Protection
Where there’s data, there’s an opening for threat actors to hold this sensitive information ransom and demand payment for its release. And it’s only getting easier to gather an increasing amount of company data online and extort it. Ransomware and data extortion are too complicated to stop with a one-size-fits-all security approach.
Our goal at Flashpoint is to stop attacks from occurring and help you if an incident does happen.
Prevention
Flashpoint’s ransomware prevention starts with understanding what the attackers are likely to do, based on the tooling, capabilities and behaviors of ransomware groups, using threat intelligence. As a security analyst, you need to know how attackers use common malware and cybercrime methods to gain a foothold in your organization and the vulnerabilities that pose the greatest risk.
Readiness and response
Flashpoint helps you develop readiness and response strategies to defend against ransomware and extortion. Our services include customized response and recovery of internal systems in the event of a ransom, as well as evaluating and testing preparedness for a potential attack. We provide research, as well as directly engaging with threat actors on your behalf.
MULTI-LAYERED RANSOMWARE ATTACK PROTECTION:
Visibility into leaked assets as a result of an extortion incident, providing you with the necessary insight into the extent of exposure and damage.
- Quickly drill into supplemental information to identify if exploits are being shared.
- See what threat actors are discussing across illicit and open-source communities.
- Identify third-party vendors who have been affected by data extortion attacks.
- Anonymously conduct investigations from a ransomware blog to verify if your organization was impacted in the incident
We conduct workshops and exercises with your stakeholders to prepare your teams for their role if an incident happens.
- Simulate scenarios, assess your plans, clarify roles, and improve coordination.
- Access to Flashpoint analysts, providing the necessary intelligence to support assessments.
- Understand and address security risks that can lead to a compromise in the first place.

Our model for ransomware likelihood analyzes newly published vulnerabilities (including thousands not listed in the public source) and uses predictive analysis to determine their chance of being used in future ransomware operations.
- Understand what software, services, and third-party assets are affected.
- Prioritize remediating ransomware-likely vulnerabilities first.
- Access to vulnerability database covering over 300,000 vulnerabilities and over sixty fields of advanced metadata.
We provide expert-led assistance in the event of a ransomware or cyber extortion incident. Our team determines the credibility of the situation, recovers systems, and assists in negotiations and payment.
Flashpoint will:
- Validate attackers claims and identify TTPs of an incident.
- Manage and undertake all communications, interactions and negotiations with the threat actor.
- Provide continuous monitoring of illicit communities during and after the response.
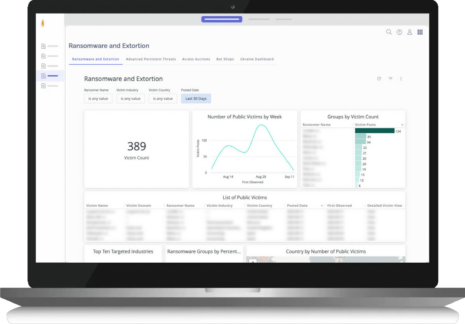
Get insights into the latest ransomware threats directly from the frontlines with access to ransomware trends, victims, and the ransomware groups themselves.
- Track the most active ransomware variants, operations and victims – specific to geography or industry.
- Visibility into a ransomers activity to see their history, trends, and pattern of life.
- Uncover ransomware groups’ primary communications, announcements about new victims, and trends across victims.
“The ransomware dashboard made my life so much easier in providing our executives with the insights they need on ransomware. It saved a ton of time too, as it’s so helpful that it can be downloaded into multiple formats, excerpted into briefings, and be leveraged into analyses.”
HEAD OF INTELLIGENCE, GLOBAL FINANCIAL SERVICES COMPANY
