Blog
Why Vulnerability Management Programs Need Visibility Into Over 300,000 Vulnerabilities

Flashpoint has been identifying and collecting vulnerabilities as they become available—with VulnDB now covering over 330,000 vulnerabilities affecting all manners of IT, IoT, and third-party libraries and dependencies. Vulnerabilities affect nearly everything, and in today’s landscape, they are disclosed by tens of thousands of researchers via many thousands of sources.
Therefore, having the full vulnerability intelligence picture is vital to effectively combat risk. However, organizations may not be aware that the full picture looks drastically different depending on where they look. The security industry often considers the Common Vulnerabilities Exposures (CVE) to be the standard for vulnerability intelligence. Unfortunately, some may not be aware of CVE/NVD’s considerable coverage gaps that severely affects its comprehensiveness, details, and timeliness. This ultimately causes those reliant on CVE/NVD to waste resources attempting to address symptoms. However, this does not necessarily address the greatest sources of risk.
CVE and NVD is missing nearly 33 percent of known vulnerabilities
Choosing to be dependent on CVE/NVD data results in your organization’s risk models missing nearly a third of all disclosed vulnerabilities:

While business leaders may be surprised to discover that CVE and NVD fail to report over 100,000 vulnerabilities, practitioners have been struggling with the inherent problems plaguing them for years. Even if they weren’t aware themselves. CVE/NVD lacks coverage of open source software and legacy software. However, it also misses critical vulnerabilities affecting widely-used products and vendors. Combining all of these deltas, we can see the contrast between the picture that CVE/NVD paints, versus Flashpoint’s collections:
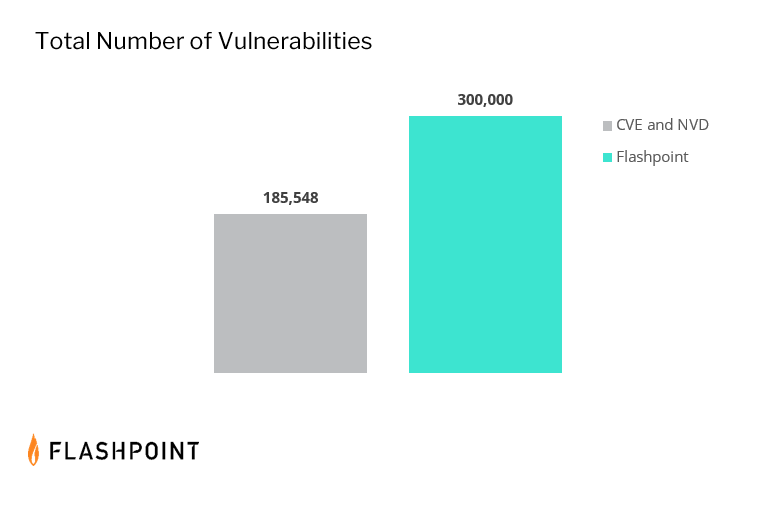
Examining the coverage gaps in CVE and NVD data
To fully understand how this delta affects vulnerability management programs, additional context is needed. Because while being completely unaware of nearly a third of known vulnerabilities is alarming, some of those vulnerabilities may not affect your organization, making it vital to examine “what” is being missed.
Many vulnerability management programs often use metrics such as the Common Vulnerability Scoring System (CVSS) to inform their prioritization processes. Even though the industry is beginning to shift away from a top-down patching approach, many organizations still find value in categorizing vulnerabilities based on their severity. However, information such as attack location, or other metadata, such as exploit status can better inform vulnerability prioritization for security teams. And while the CVSSv3 framework allows the incorporation of exploit status as part of the temporal score, that is not provided by NVD, which scores all vulnerabilities with a CVE ID.
Studying the vulnerability disclosure landscape, Flashpoint has found the following data points, at time of publishing:
- CVE/NVD misses 31 percent of known CVSSv2 scored high-to-critical vulnerabilities.
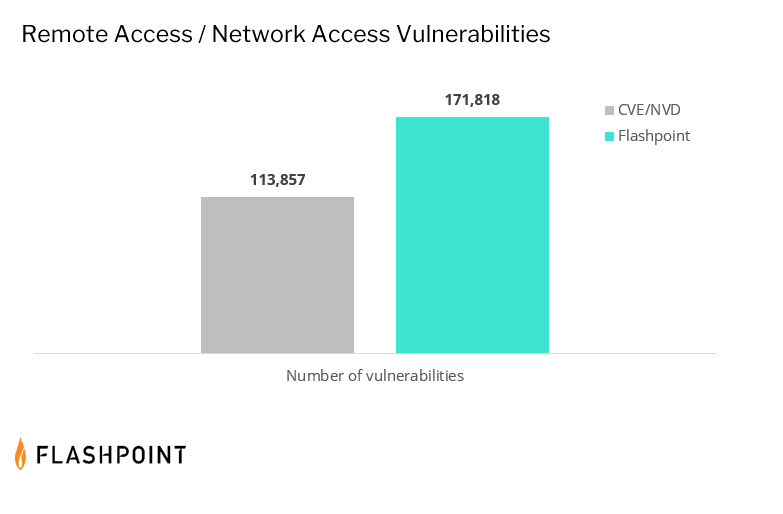
- CVE/NVD misses 33 percent of known, remotely exploitable vulnerabilities.
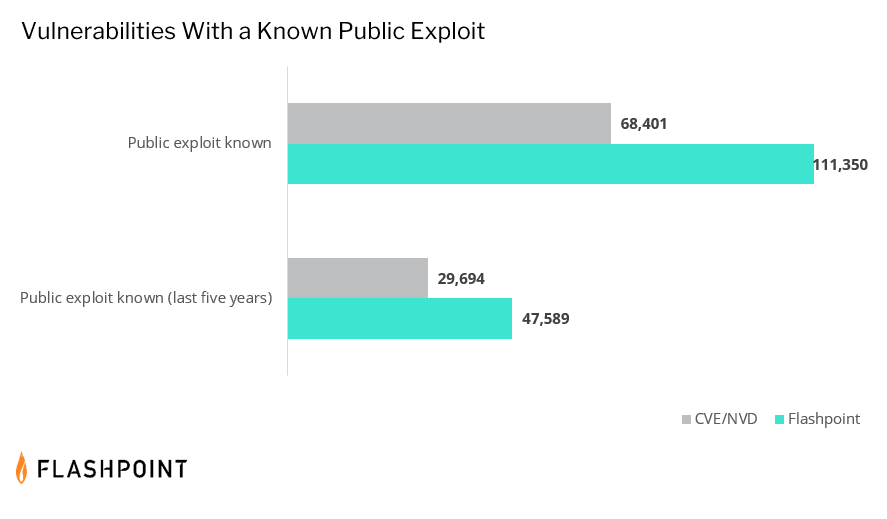
- CVE/NVD misses 38 percent of known vulnerabilities with a public exploit.
Here are side-by-side comparisons demonstrating the differences between CVE/NVD and Flashpoint’s collections on a more granular level:
CVE/NVD’s coverage gaps based on CVSSv2
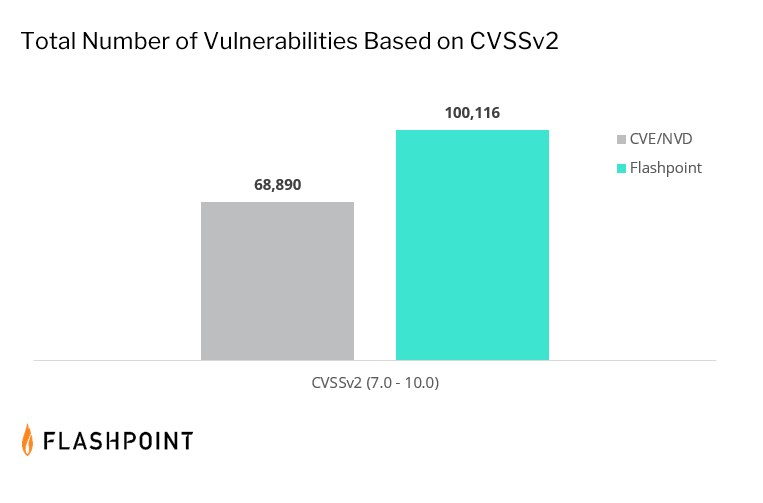
CVE/NVD fails to report 31 percent of known high-to-critical scored vulnerabilities (CVSSv2). This subset of data includes well-known products and vendors. This discrepancy suggests that organizations solely relying on CVE/NVD may have a false sense of security, as there may be critical vulnerabilities potentially affecting their assets that they have no visibility of.
CVE/NVD’s coverage gap based on exploitability
Recent activity from the Cybersecurity and Infrastructure Security Agency (CISA) shows the increasing role that exploitability has in guiding risk-based vulnerability management processes. Threat actors are actively exploiting vulnerabilities, and sometimes the exploits they choose to weaponize fall outside traditional vulnerability management frameworks. Because of this, security teams need to both address highly exploitable issues, while also remediating the vulnerabilities in their queues.
However, in order to execute this, vulnerability managers need quality intelligence to prioritize effectively. But for those relying on CVE/NVD, they will be missing a third of known remotely exploitable issues. Worse yet, they will also be missing over 38 percent of known issues with a public exploit. This percentage delta is consistent even when limiting the time period to the last five years.
Enhance vulnerability management programs with Flashpoint
To address the root causes of risk, organizations need the full vulnerability intelligence picture. Relying on CVE/NVD data will cause organizations to miss nearly a third of known vulnerabilities, and it is impossible for security teams to defend against issues they have no visibility into. To better protect their networks, enterprises need comprehensive, detailed, and timely intelligence. Sign up for a free trial today to get access to Flashpoint’s collection of over 330,000 vulnerabilities that affect all manners of IT, IoT, and third-party libraries and dependencies.