Blog
Situational Awareness in Russia: Neo-Nazi Mercenary Groups, PMCs, and Illicit Financing
Russian mercenary groups and private military companies are operating in Ukraine, including the “Russian Imperial Movement” (RIM), “Wagner Group,” and Task Force Rusich.

OFAC and illicit financing
In a series of designations last week, the US Department of Treasury named Task Force Rusich, a neo-Nazi paramilitary group that has participated in combat alongside Russia’s military in Ukraine. Alexey Milchakov and Yan Petrovsky, who founded the militia in 2014, were included on an updated SDN list from OFAC, which also disclosed five cryptocurrency wallet addresses connected to Task Force Rusich—two Bitcoin, two Ethereum, and one Tether.
Flashpoint’s intelligence team—which includes support to anti-money laundering (AML), counter-terrorist financing (CTF), and know-your-customer (KYC) compliance programs—has been aware of Task Force Rusich and its illicit funding effort since the beginning of the full-scale invasion of Ukraine. By triangulating blockchain and threat intelligence related to mercenary groups like Task Force Rusich, Flashpoint can provide important context into on-the-ground operations, including troop movement; communication and transaction methods; arms, supply, infrastructure needs; other crucial insights into Russia’s war on Ukraine, which is now more than 200 days long. This type of real-time open-source intelligence is vital to governments and commercial enterprises with vested interests in Russia, Ukraine, and nearby regions.
Task Force Rusich and other Pro-Russia mercenary groups
There are at least three Russian neo-Nazi and white supremacist mercenary groups likely operating in Ukraine, including the “Russian Imperial Movement” (RIM) and “Wagner Group.” Task Force Rusich is reportedly also affiliated with the Wagner Group, a private, neo-Nazi-affiliated, Russian military mercenary group that has operated since at least 2014, when it assisted the Russian military during the annexation of Crimea. And, according to a report by the New America think tank, Task Force Rusich is also affiliated to the “Union of Donbas Volunteers”, a group founded by Alexander Borodai, a former Russia-appointed separatist leader in the Donetsk region who is now a lawmaker in President Vladimir Putin’s party. Task Force Rusich was also reportedly founded in 2014 by two graduates of RIM’s paramilitary training unit, Partizan. The group operated in the Donbas (Donets Basin) region of eastern Ukraine in 2014 during the fighting between Russian separatist forces and Ukraine.
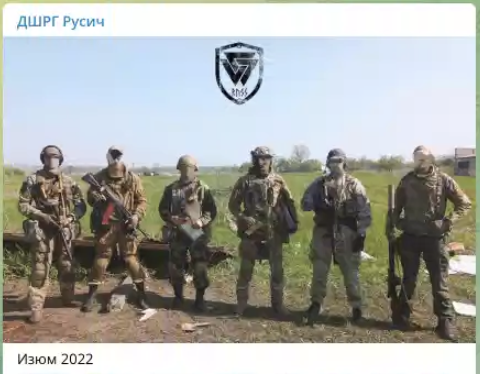
During this war, Task Force Rusich has been operating in Ukraine since at least April of 2022. Rusich members were active in the Ukrainian city of Izyum as of July 2022. A mass burial site found after the liberation of the city in September contained more than 440 bodies, many with signs of torture.
Financing
Russian mercenary groups and their supporters are often engaged in online fundraising activities, raising funds for military and tactical equipment, medicine, and care for the wounded. Most of the observed fundraising activities occur through Russian bank cards, but these groups also use cryptocurrency and a crowdfunding platform.
Some supporter groups also sell merchandise with their logos and the logos of the paramilitary groups. The mercenary unit Task Force Rusich, for example, persuades its supporters to donate to their cause through cryptocurrency donations to help Russia’s territorial targets in its war against Ukraine. According to our blockchain intelligence, the crypto wallet addresses disclosed by OFAC are only a part of Task Force Rusich’s use of blockchain technology to fund its efforts.
Related: Funding and the Russia-Ukraine War: KYC for Crypto Transactions Proving Difficult
One Rosich Ethereum donation wallet, which the US Treasury disclosed on September 15, provides a window into how Russian mercenary groups transact using cryptocurrency. This wallet was newly funded on September 7 with about .67 Ethereum (~$922). Two days later, with fresh funds at its back, Task Force Rusich posted a list of the military equipment it needed for an unspecified unit in the “Northern Military District”—likely code for Kharkiv, Sumy, and Kyiv regions, which includes the Ukrainian cities of Kharkiv and the capital, Kyiv. Then, two days after that, on September 11, a Task Force Rusich ally announced that the same wallet had received donations of more than $20,000.
Russian PMCs
Russia has used private military companies, or PMCs, affiliated with the Russian government via unofficial means to aid war efforts in several countries, lessen official casualty numbers, and maintain plausible deniability about the actions of the Russian Armed Forces. The February invasion of Ukraine has led to a rising profile of these PMCs and paramilitary groups as the Kremlin is relying on them increasingly heavily. However, the presence of several uncoordinated groups in Ukraine—including PMCs, regular troops and troops of the National Guard, a law enforcement unit specializing in riot control—has reportedly led to confusion on the ground. Paramilitary groups have also been called responsible for war crimes committed in Ukraine.
PMCs and associated paramilitary groups have actively built an audience in Russia, including through their presence on Telegram, VK and other social media platforms. Rusich has been particularly prolific in this regard: apart from its main Telegram channel, one of its known fighters, Yevgeny Rasskazov, alias “Topaz” also maintains a channel with more than 40,000 subscribers. In recent months, the Wagner Group also started to recruit openly in Russian cities and prisons where it is offering a commutation of sentences if recruits survive six months of warfare in Ukraine, highlighting the group’s links to the authorities. The “Reverse Side of the Medal” Telegram channel has also argued against general mobilization in Russia, likely because this would lessen the influence of the companies in the context of the war in Ukraine.
Get Flashpoint on your side
Any organization’s security capabilities are only as good as its threat intelligence. Flashpoint’s suite of tools offer you a comprehensive overview of your threat landscape and the ability to proactively address risks and protect your critical data assets. To unlock the power of great threat intelligence, sign up for a demo or get started with a free trial.